Quintius Walker, Grey Hat Developer, Cybersecurity Consultant
17 August 2025
Photo by DALL-E
Absolutely everything on this blog pertaining to the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING ACTIVITY!
Before we explore today’s vulnerability, let me reintroduce what we’re building and why it matters….
You ever build something that feels like a calling more than a product?
That’s what ChifuAI is.
It’s not just a wellness app. It’s a digital companion for inner transformation– a combining the movement of ancient wisdom with machine learning.
ChifuAI is designed for practitioners of Qi Gong, Tai Chi, and internal martial arts who want more than just videos and timers. This platform listens. It observes. It guides.
ChifuAI is built it to:
– Track your breath and nervous system in real-time
– Offer personalized feedback on your form, your flow, your chi
– Help you log your emotional state and energy shifts
– Recommend sequences and breathing styles that match you
And all of this is grounded in mindfulness.
Not monetization. Not hustle culture.
Just pure, centered, intentional practice.
But…
If we’re going to create a tool that honors the sacred, we also have to make sure it’s secure.
Because where there’s breath and data, there’s risk.
And where there’s access, there’s the potential for abuse.
Which brings us to today’s topic:
BFLA – Broken Function Level Authorization.
Let’s unpack what it is, why it matters, and how the wrong access at the wrong level can wreck a system… even one designed to help you heal.
The Hidden Open Doors: Understanding BFLA in Mindful Tech Systems

Now if you read the last piece on BOLA, you already know we made a clear distinction between authentication (who you are) and authorization (what you’re allowed to do).
But authorization isn’t a flat surface.
It’s a multi-tiered temple.
Different roles. Different access. Different power.
And this is where a lot of systems slip.
When you see a u-r-l
and an object’s
being referenced,
If you’re out
hunting bugs then it’s
no time for eating breakfast.
Or an i-d
being passed
through the body of a request,
Let’s leave no room
for guessing
this isn’t a question if we should test.
It’s all about
can you perform an action,
you shouldn’t be able to perform….?
And if you perform that action,
Tell me,
Did it deviate from the norm?
If you’re not a moderator
chosen in the forum,
I don’t mean no harm
but,
you should not be dropping posts….
There’s no way
you should be messing
with the passwords, NO!
Or in our Zoom calls
locking out the hosts.
Let’s break it down with a real-world metaphor:
Imagine you’re at a Shaolin temple.
-
A student may enter the training hall and the outer gardens.
-
A monk can access the scroll chamber and lead meditation.
-
A Shifu? He’s allowed in the sacred archives. The ones behind the iron doors — wisdom passed down in whispers.
Now let’s say a student figures out that if they just enter a URL meant for the Shifu’s dashboard, the system lets them in.
No challenge.
No elevation check.
Just a cracked-open backdoor leading straight into sacred space.
That right there?
That’s BFLA.
Broken Function Level Authorization.
It’s when the system doesn’t verify if you have permission to access higher-level functions or administrative features — it just lets the request slide through like you’re already on the list.
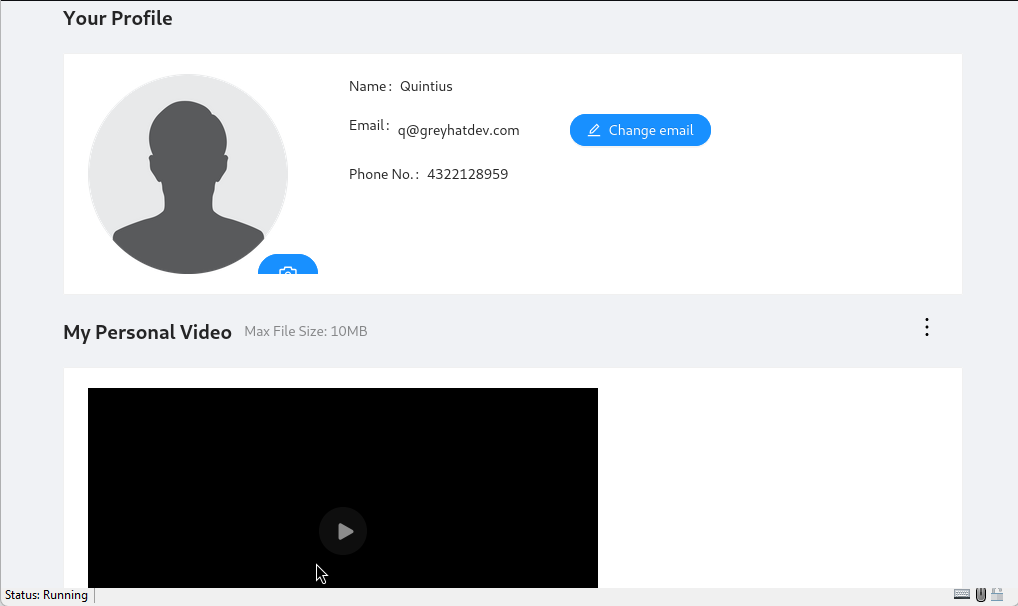
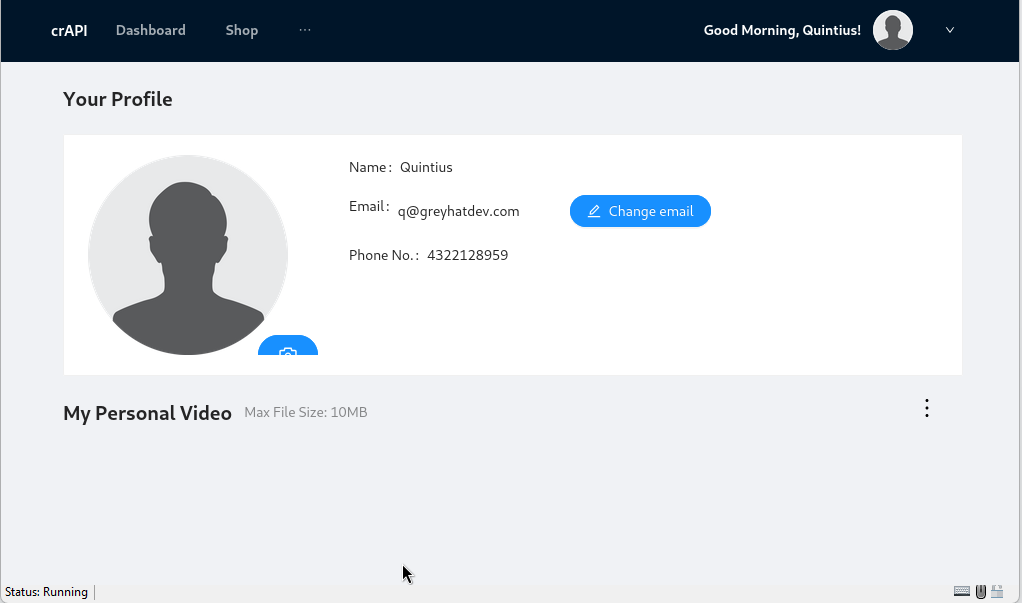
So, sticking to our grind we have going with TCM Academy on hacking APIs, and to demonstrate a BFLA vulnerability, first we’ll add a video to our dashboard, or portal.
When we look at this exchange in our proxy we’ll take note of the id number in the Response. In this case it’s 52. Our goal in this case is to try and delete it.
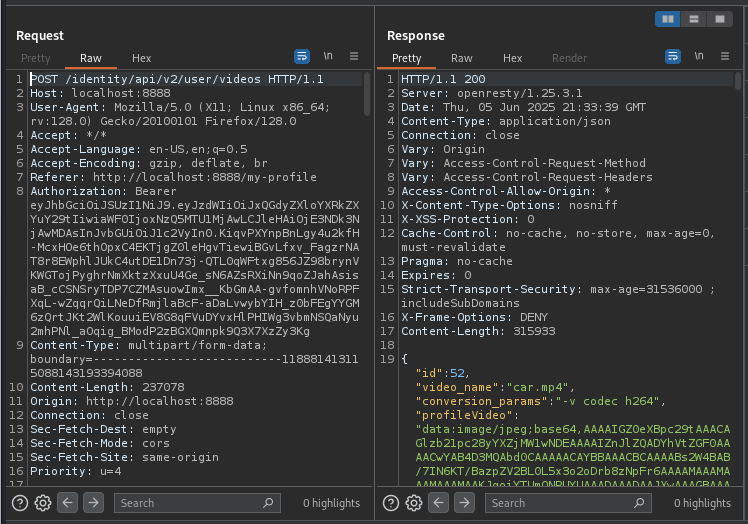
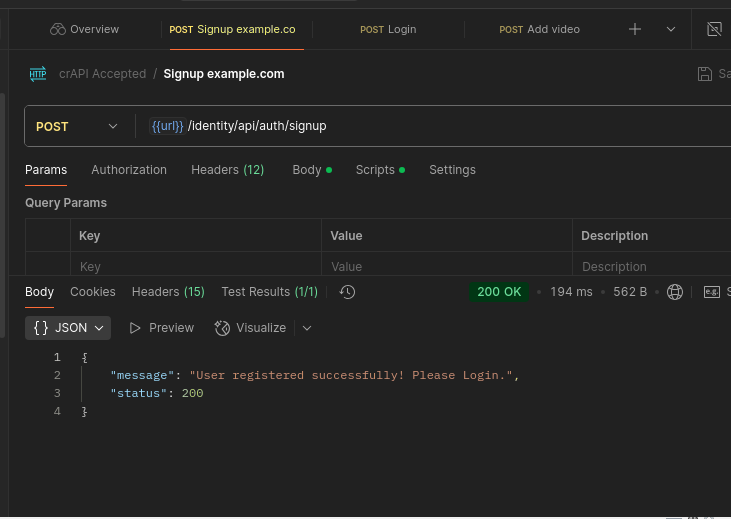
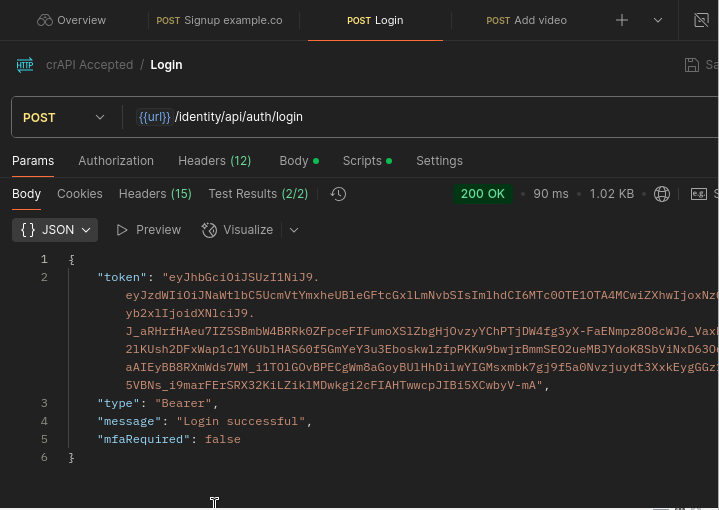
Next we’ll go over to Postman and sign up for a new account. After we see that we have registered successfully, we can log in to verify our token and we’ll be set up to proceed to our next step in the test.
Now we can upload a video for this new user to test with. After we add the video, we’ll issue a GET request to test that it’s uploaded and working. (Notice the POST and GET requests.)
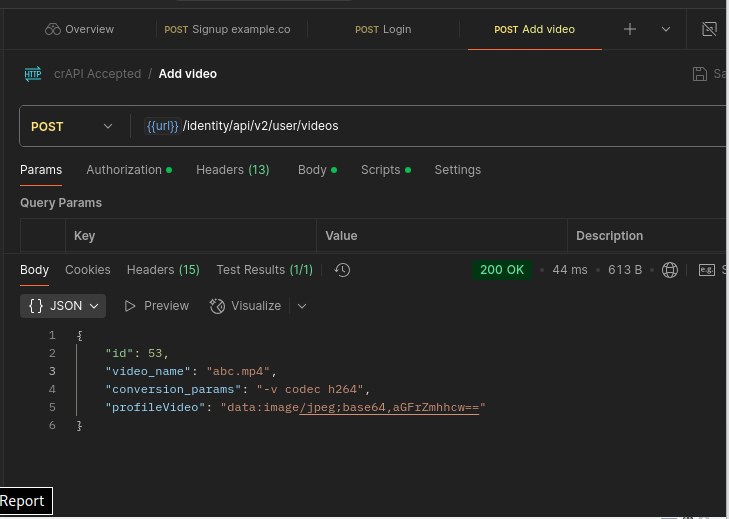
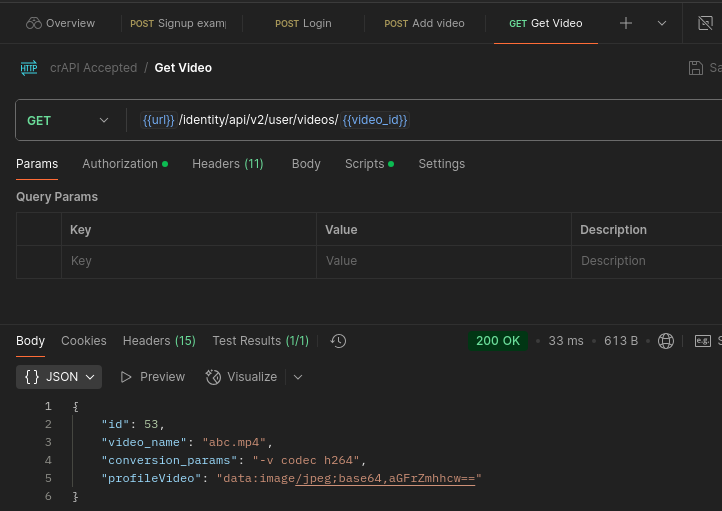
Perfect.
Now, when we first try to delete the video, we get a message with a status 403 (Forbidden) and informing us that this is an administrative function and that we should try accessing the admin API.
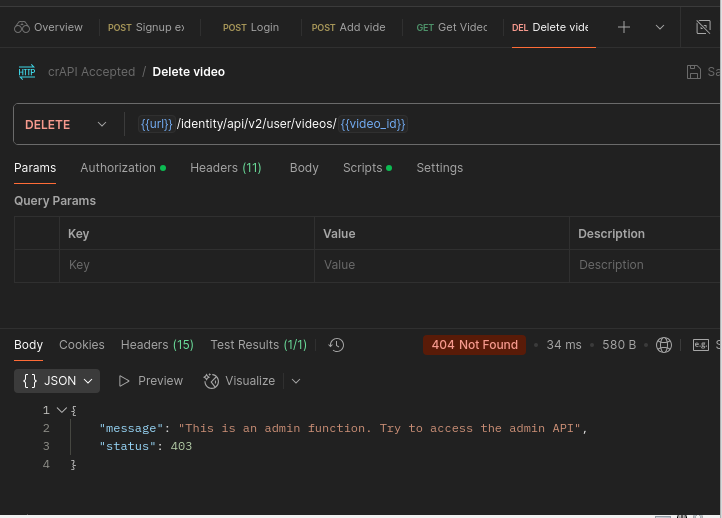
The following screenshot wouldn’t really make sense without a bit of elaboration of what actually occurred.
Aside from the message that is returned which, by the way is the easiest win we’ll ever see since they practically told us how to get around our restriction, take a look at the url.
/identity/api/v2/user/videos
It isn’t depicted but there was an endpoint labeled “Delete video by admin” and it just so happened to look like this:
/identity/api/v2/admin/videos
By simply replacing “user” with “admin” in our url, we were able to execute an elevated function, like deleting data.
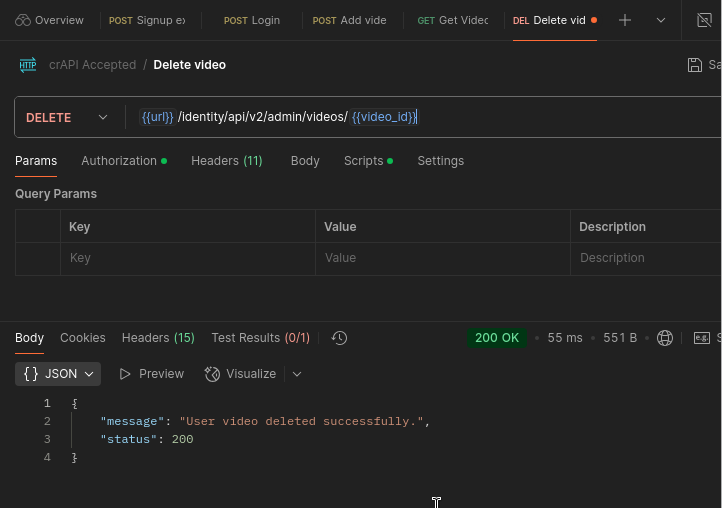
Now that we’ve established that we can carry out functions at elevated levels with this endpoint, we can now simply choose the id of the video we’d like to delete which, remember in our case was 52, and fire off to reveal our finding of a BFLA vulnerability.
Why It Matters for Apps Like ChifuAI
In an app like ours — where instructors, students, and clinical experts may all be using the same platform – role boundaries must be sacred.
A student shouldn’t be able to:
-
Access unpublished sequences submitted by masters
-
Edit community journals
-
Pull energy reports from other users
-
Interact with system-level configuration files
-
Simulate feedback as if they were a credentialed Shifu
If we don’t validate what level of function each user can access, the entire ecosystem collapses.
Why This Matters in AI and Health Ecosystems
When we train our systems to teach, to observe, to guide – we have to make sure they don’t forget their boundaries.
ChifuAI isn’t just giving access to videos or forms. It’s shaping behavior. It’s reading states of being. It’s helping people become more embodied, more aware.
That means every endpoint, every permission, every function needs to honor digital integrity the way we honor chi, with structure, flow, and alignment.
Broken Function Level Authorization is when that alignment breaks down.
And in our Sangha, we work hard to not let that happen.
If this post made you pause…
If it helped you see the layers beneath your login screen…
If you’re building apps, or just trying to breathe a little deeper in this digital storm…
Then join our Sangha.
The Chifu Dharma Newsletter is where tech meets tranquility.


