Quintius Walker, Grey Hat Developer, Cybersecurity Consultant
7 April 2024
Photo by Markus Spiske on Unsplash
Absolutely everything on this blog pertaining to the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING ACTIVITY!
My Reflection Over Command Injection – Part 1
Security weaknesses that allow attackers to inject commands are some of the most dangerous. These types of vulnerabilities grant attackers the ability to run commands on the back-end server, potentially jeopardizing the entire network. Although many types of injection vulnerabilities exists in web applications, the one we’ll be focusing on in this article is called OS Command Injection.
Injection vulnerabilites can happen because some features in web applications allow user input to run commands directly on the computer. Even though there are cases where these commands might be used for routine tasks, if the website isn’t careful with what users can type in, attackers can sneak in their own commands and wreak havoc.
Let’s look at an example….
The following screenshots were taken as I worked my way through the Command Injection module in HTB’s Certified Bug Bounty Hunter.
They wonder what’ll take for me to write another hit again,
I grab my pen then
I open up Obsidian.
Cause it ain’t promised I’ll be working as a C-A
the way I see that, black
is that my back’s against the D-A.
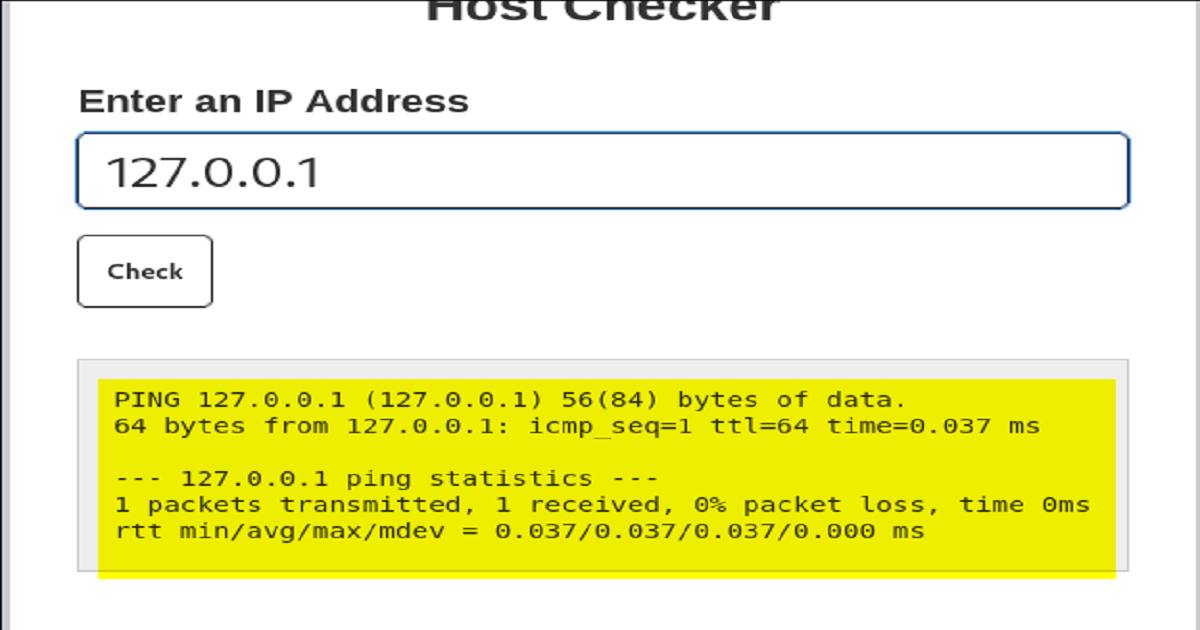
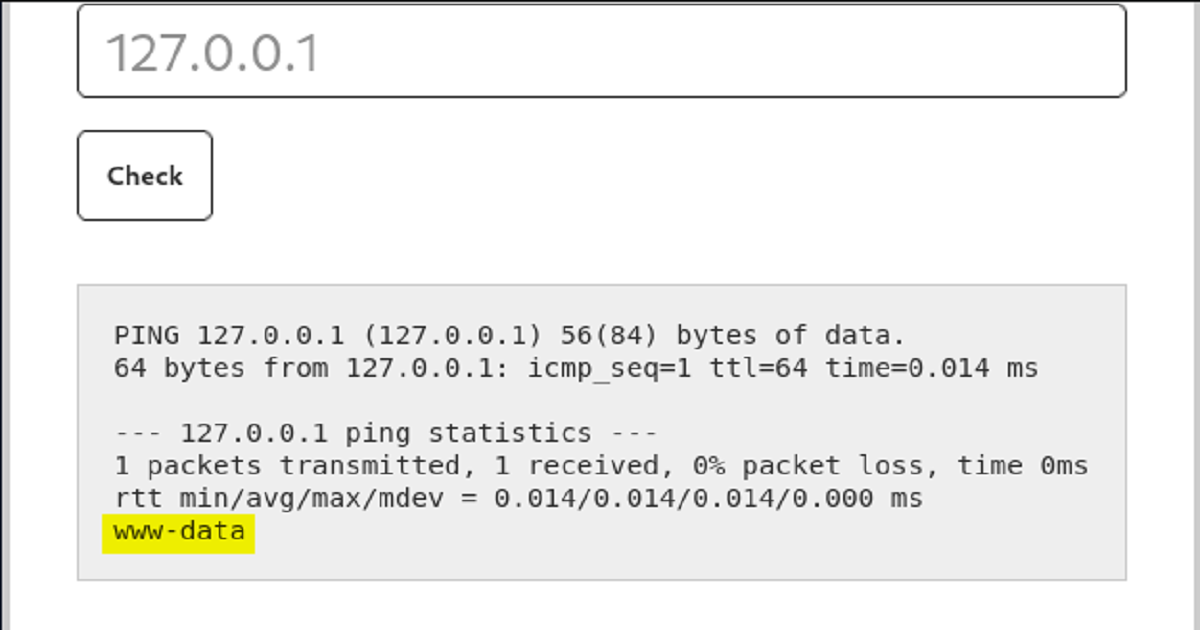
The first of the above screenshots show a web application that accepts some input from a user, executes the input on the back-end server, and then returns the result of the command to the front-end of the web application.
In this case, a user types in an ip address and clicks a button to send the input to the server, which, upon receipt executes the ping command and returns the result.
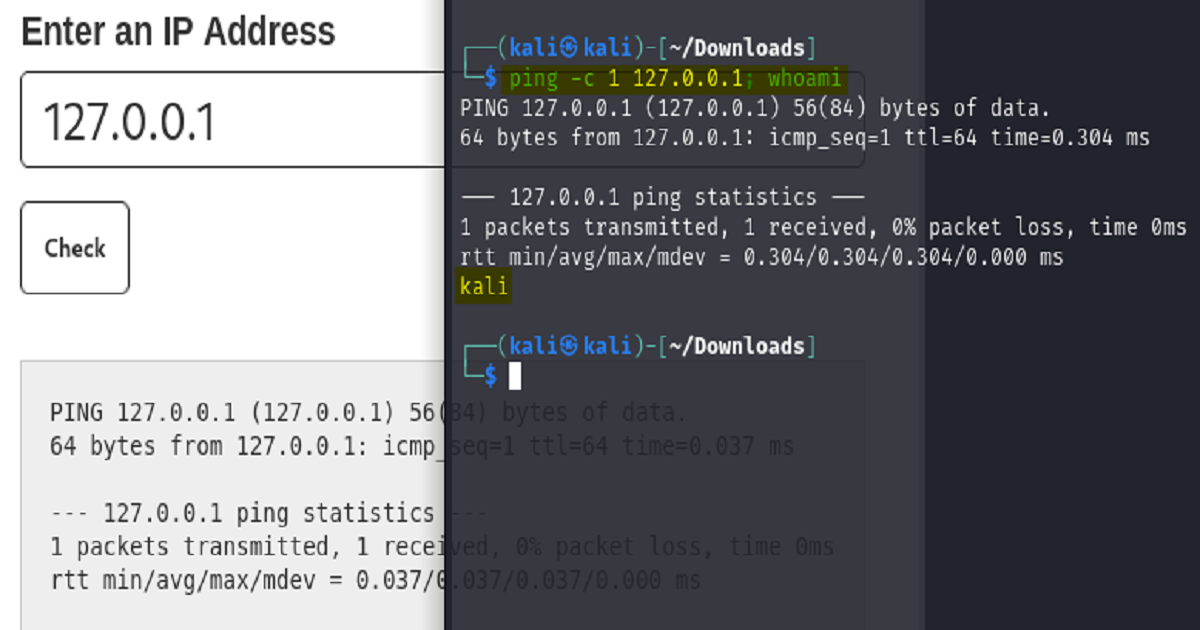
The second of the two screenshots show that if we append ; whoami to the ip address the command runs successfully and delivers our result. This proves to us that we are able to inject system commands into the web application and have the back-end server execute them.
Let us try the same commands from the front-end of the application by entering them as input to the text box.
Cause he wait,
for me to make a trip but that’s not happening,
I flipped the script….
so why you think that I’m not rapping, man.
It ain’t no way that I’m gon end up in that trap again,
They say Allah controls ya fate
I just keep hacking, man.
Exploiting Application Program Interfaces,
But it’s all legal so we won’t be catching cases.
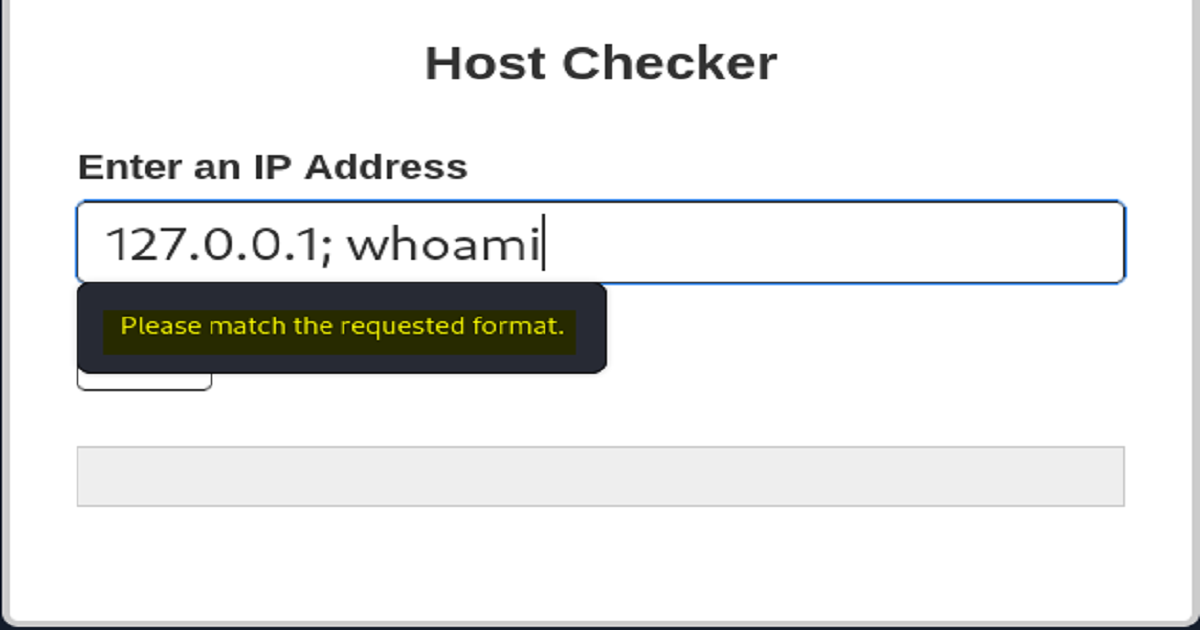
As you can see from the above screenshot, the application refused to accept the input and throws an error. However, upon examining the source code we realize that despite the error message being displayed, there was no input sent to the server and thus no response is being returned from the server. Therefore, the input is being validated on the front-end, which we know can easily be bypassed.
Let’s use a proxy like Burp that’ll allow us to intercept the request before sending it along to the server. (We’ll also encode our command to ensure it’s accepted and processed.)
I put the hack to poetry
they tell me it’s not literal,
so let’s attack a type of vuln
that’s known as critical.
Injection….
Where sys commands can execute directly,
on the back-end server
make the sys admin respect me.
Cause if the app use
user input to retrieve and return
we may subvert commands that’s intended,
with ones that we learn.
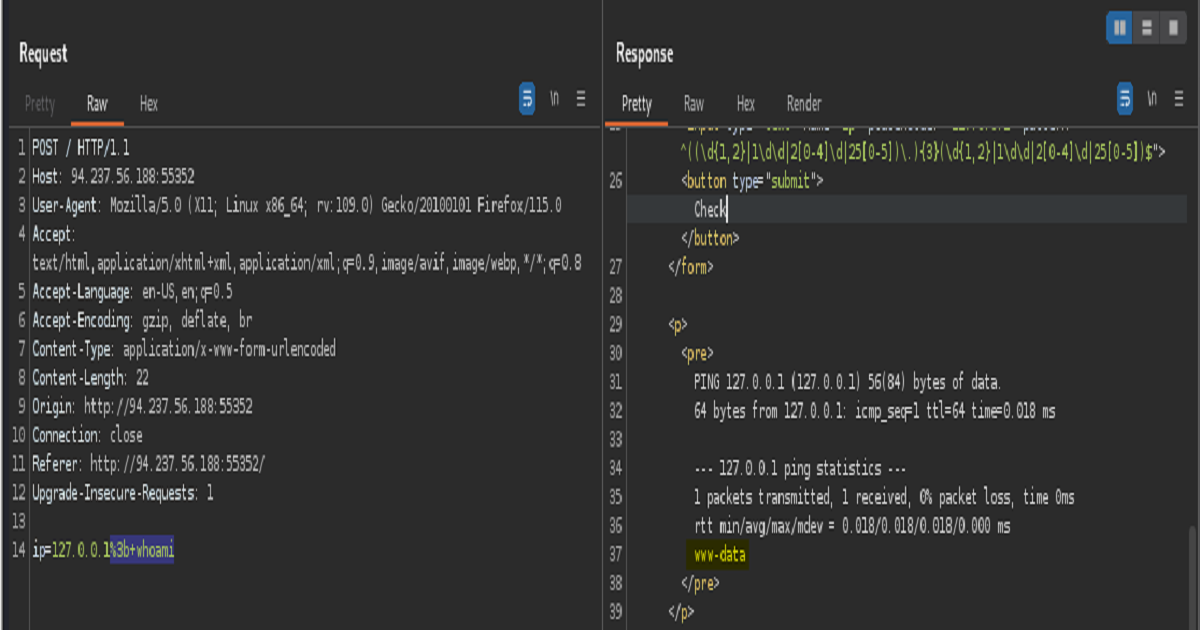
Finally, as can seen above, by intercepting our payload with a proxy before sending it to the server we were able to bypass the frontside validation the web application had in place. Hence proving the web app to be vulnerable to command injection.
Here’s the command shown successfully executed on the front end.
This was a very small and basic example. In our upcoming post we’ll take a look at some more examples as we continue grinding through the Bug Bounty Job role path.
I hope in this article was able to bring a bit of enlightenment around OS Command Injection. Thank you for reading and by all means don’t hesitate to reach out with any questions you may have regarding any parts of this post that you find is still as clear as mud.
Hack On, Ladz & Gentz!


