Automated Reconnaissance with Sparta

Grey Hat Developer
16 January 2017
As a security tester you should ensure that you understand a tool before using it in an actual security test. Some tools may return information that is out of scope, or out of agreed upon terms of the test, and thus should not be used. In this post we’ll be looking at performing automated reconnaissance with Sparta.
Scanning with Nmap and Metasploit to enumerate services and find vulnerabilites (often times even exploit them) is all fine and dandy. However, the question I often get from a lot of beginners and those who are hackers by hobby as opposed to hackers by trade is, “Isn’t there an automated tool that I can use to kill a few birds with one stone?” My long winded reply to this question is usually something along the lines explaining how automated tools can be very helpful in certain situations but should never be the only tool that you rely on to carry out your testing. Also, the results gathered from these tools and scans should never be the only results you take and run with as being conclusive. Having said that, my short answer is, yes! I would now like to introduce to you a tool by the name of Sparta.
Screenshot of Sparta being started and opened from the terminal.
Use ctrl + to enlarge image
When listening to these request for automated tools I’ve come to realize that often times the beginner is intimated by having to type commands into a terminal more than anything. So more times than not what they’re really asking for is a GUI-Graphical User Interface. That’s where Sparta comes to mind. Sparta is a GUI tool that can be used for network scanning, enumeration, and attacks. What this tool does is scan systems for open ports and services information. Interestingly, not only can this tool detect vulnerabilites but it also provides access to tools for security testing. Let’s have a look at this tool in action shall we?
“The best place to get information about the other side is from the other side”
In Kali you can start Sparta by either typing “sparta” in a terminal as I’ve done in the above screenshot or you can just go to the menu and find it. You’ll want to click, “Click here to add host(s) to Scope” and enter the IP address of the target in the pop up box. You can also add multiple IP’s by separating them each by a space as I’ve done in the screenshot below. Once you’re done just click, “Add to Scope“. Sparta will automatically start multiple nmap scans of the specified systems looking for open ports and service identification.
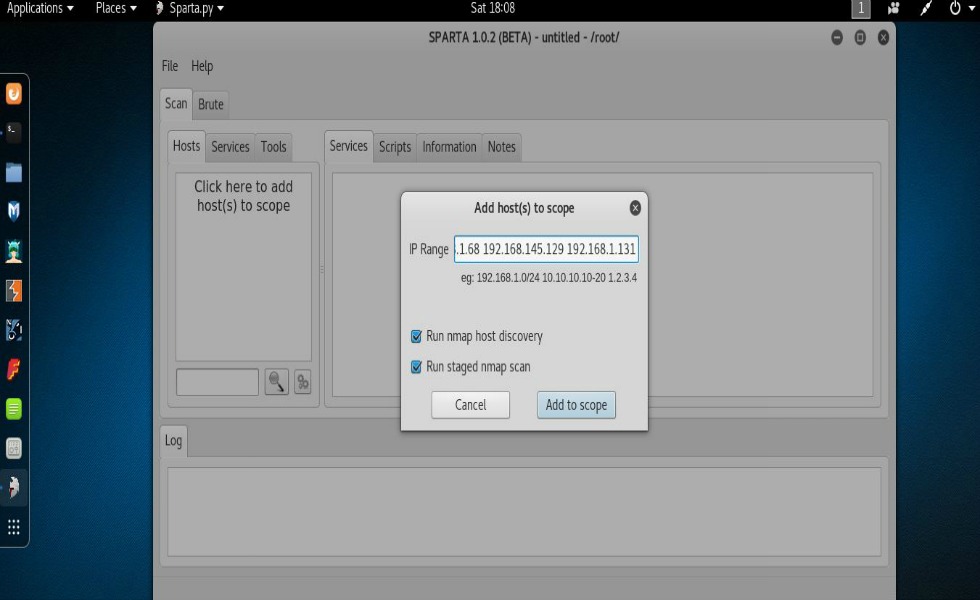
Adding hosts to scope in Sparta.
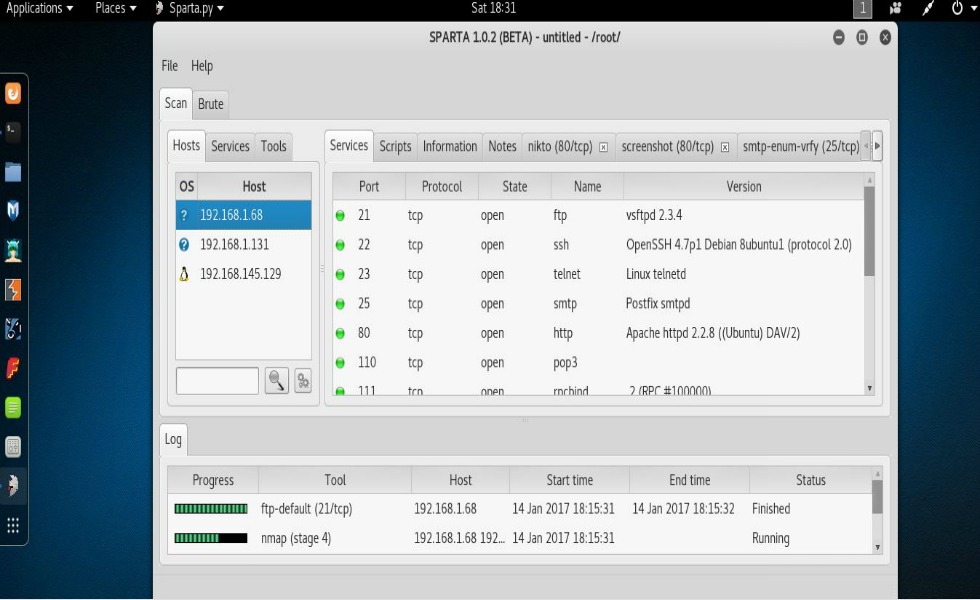
Information returned from Sparta scan.
Notice that the information returned by Sparta is neatly categorized on both the left and right sides of the screen. Also returned under the “Services” tab is a complete list of services running on the systems scanned along with ports used and their version numbers. Interestingly, under the “Tools” tab you can see the results of several automated attack tools. For example, there was an ftp service running on one of the systems. Sparta went ahead and done us the pleasure of checking the service for standard usernames and passwords. As you can see from the screenshot below, Sparta was indeed able to find standard usernames and passwords being used on one of the systems that I scanned in my network. Of course this system was vulnerable on purpose for the sake of testing but keep in mind, if this were an actual system of a client that we were security testing for, Sparta has very quickly allowed us to see numerous vulnerabilities.
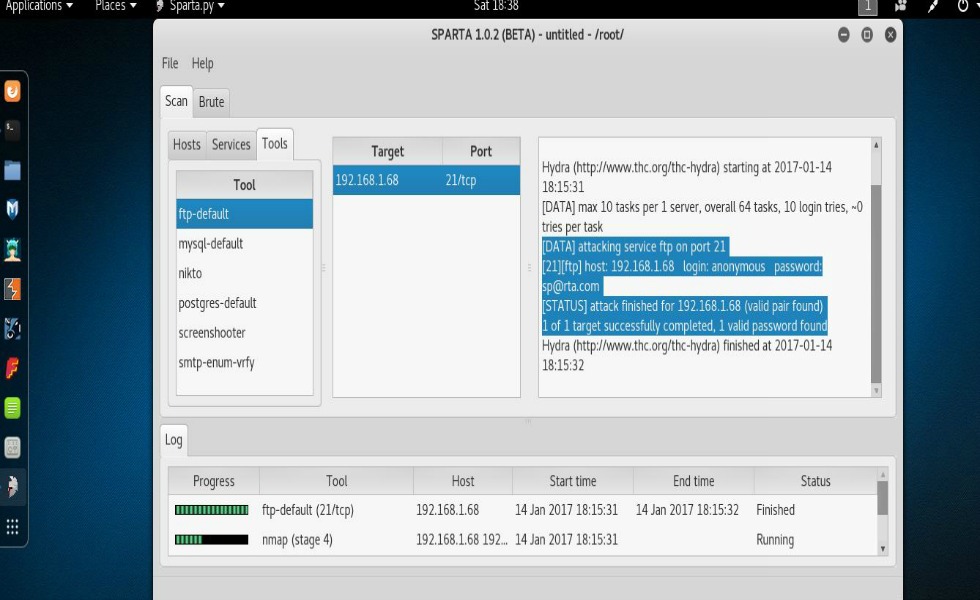
As we’ve just seen, Sparta is a nice GUI tool that provides for network scanning, enumeration, and in some cases even attacks. Businesses and end-users are being better educated when it comes to securing their systems but that doesn’t mean that as a security tester you shouldn’t still at least test for them. Afterall, that is your job, right?
I hope this post has been useful. Feel free to comment or connect with me on Twitter and by all means, please subscribe. Thank you for reading and as always, Hack On, gents!
