Before we go further into any more of the technical aspects of hacking, I want to point out that normally, hacking is a process. This remains true for the individual hacker as well as for the collective hacker group. The majority of people I meet, before being educated about the “process” of hacking, are under the impression that a successful compromise is carried out spontaneously. This is so far away from the truth. In fact, even the process itself can be broken down into five separate phases.
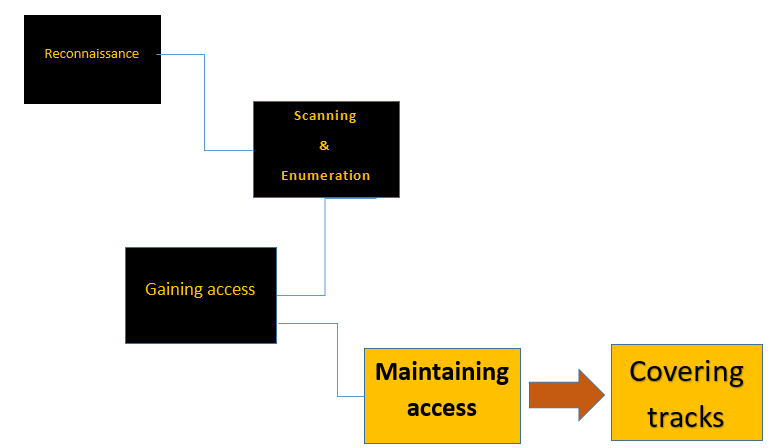
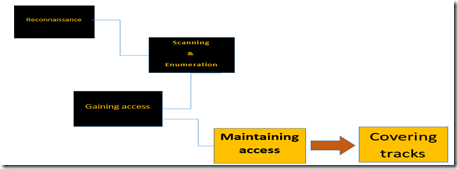
In subsequent posts we’ll cover some of the techniques and tools used by a hacker within each of these phases. For now, I just want you to be aware that they do exist. You may hear these phases called by different names by different people but regardless the terminology used they still exist. I also want to point out that the phases aren’t altogether linear. What I mean by this is that some of these phases run concurrently and continuously throughout a hack. The phases are:
Phase 1- known as the reconnaissance phase. This is nothing more than the steps taken to gather evidence and information on the targets you wish to attack. In Phase 2- scanning and enumeration, a hacker takes the information gathered in recon and actively applies tools and techniques to gather more in-depth information on the targets. In Phase 3- the gaining access phase, true attacks are leveled against the targets enumerated in phase 2. In phase 4- maintaining access, hackers attempt to ensure they have a way back into the machine or system they’ve already compromised. And in the fifth and final phase, covering tracks, attackers attempt to conceal their success and avoid detection by security professionals.
It’s worth repeating here, that contrary to popular belief, hackers do not just randomly assault things hoping to find some overlooked vulnerability to exploit. As I mentioned above, hackers follow a specific, organized method to thoroughly discover every aspect of the system they’re targeting. This method, and some of the tools and techniques that hackers use along this process will be covered in later posts. For now…just be aware that hacking is a process. Rome wasn’t built in a day!