Authentication & Authorization Attacks: Part 1
12
October, 2023
Practical Bug Bounty: Authentication & Authorization Attacks- Part 1
Photo by Markus Spiske
Everything, and we mean absolutely everything on this blog that surrounds the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL ACTIVITY!
Once upon a time there was an interview where a recruiter emphasized the importance of candidates knowing when to course-correct. At Grey Hat Developer we wholeheartedly agree and add that not only candidates, but everyone should know the skill of course-correcting.
In fact, we agree so much that we’ve updated our navigational system.
Hence, moving forward the pursuit of the PNPT (Practical Network Penetration Tester) has been paused citing it not being mission critical to our time or budget.
But why the sudden shift? Great question!
As you know we aspire to specialize in web application security, not just general penetration testing. And as fate would have it, TCM Security has partnered with Intigriti to release the Practical Bug Bounty Course.
Thus, another opportunity has opened for our D3v’z to sharpen their axes with more practical experience!
So, let’s dive right in and see whassup!
I’m going to be tackling this course as close to play by play as possible. Thus, I’ll be keeping pace with the instructors and the first web attack vectors we’ll be looking at are Authentication and Authorization. I won’t spoil it for you and tell you what the instructor used as an example of the differences between the two, but I will give you an example of my own that I like to use.
A lot of streets dudes that I know, when they travel to other cities, have a system called “checking in.” The process looks a bit like this:
Hacker X wants to network for more hackers to bring into his organization so he travels to Houston, Tx and visits an infamous neighborhood called 5th Ward. There he encounters a group of gatekeepers. (In this case we’ll call them city-keepers).
The city-keepers surround Hacker X demanding to know “who” he is. Hacker X provides that information and is then asked to wait while they consort with the Database of Networked Hackers to confirm his affiliation with 5th Ward. The gatekeepers find that Hacker X is indeed known in the neighborhood, so they allow him pass through the gates.
This part of the process defines authentication. Hacker X is authenticated into the neighborhood.
Now before letting Hacker X go about his way, the city-keepers pull up a list on their tablets detailing all the things he can do and places he is allowed to frequent while he is there networking. They also inform him of the items he’s allowed to bring and leave with into and out of the neighborhood.
This is authorization. Hacker X is being authorized into the neighborhood.
In short, authentication defines who is allowed while authorization defines what is allowed.
By the way, on some of the exercises you’ll notice that I completed using Burp Suite and Zap Proxy <– which can be found here.
Here’s a couple of screenshots on how to get Zap Proxy downloaded and installed on Kali 2023. It consists of downloading the current version, changing permissions, and making everything executable.
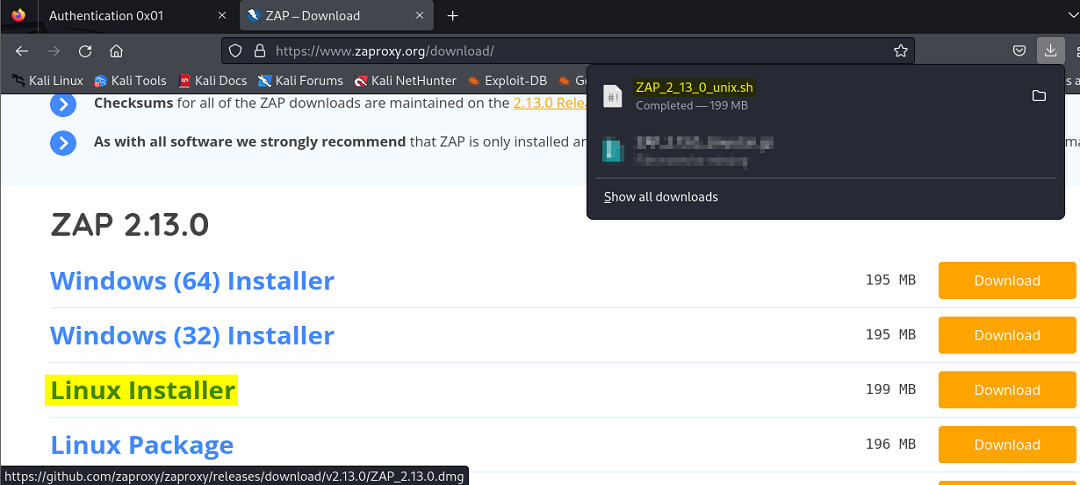
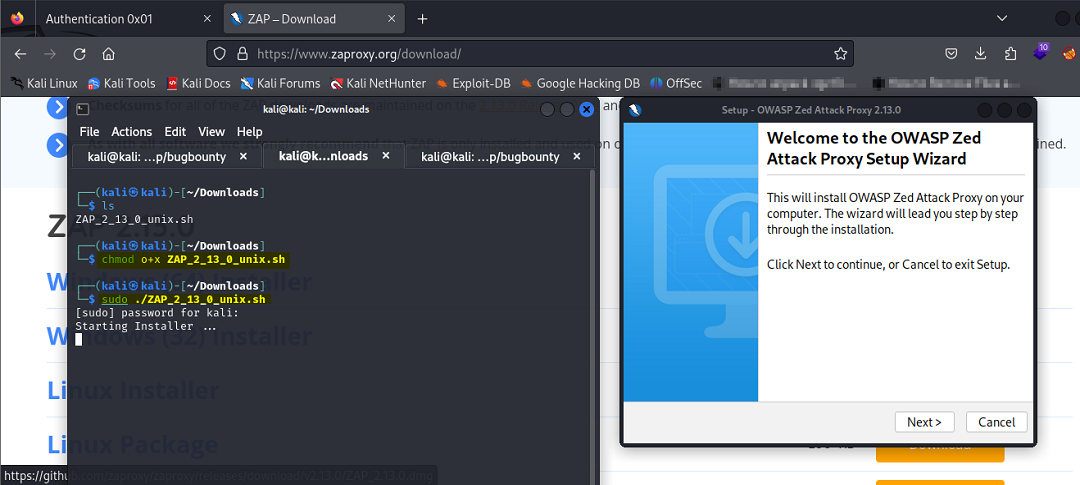
Auth 0x01
In our first example we looked at Fuzzing and Brute Forcing. As we know there’s tons of tools to accomplish this task but used Burp Suite and Zap Proxy.
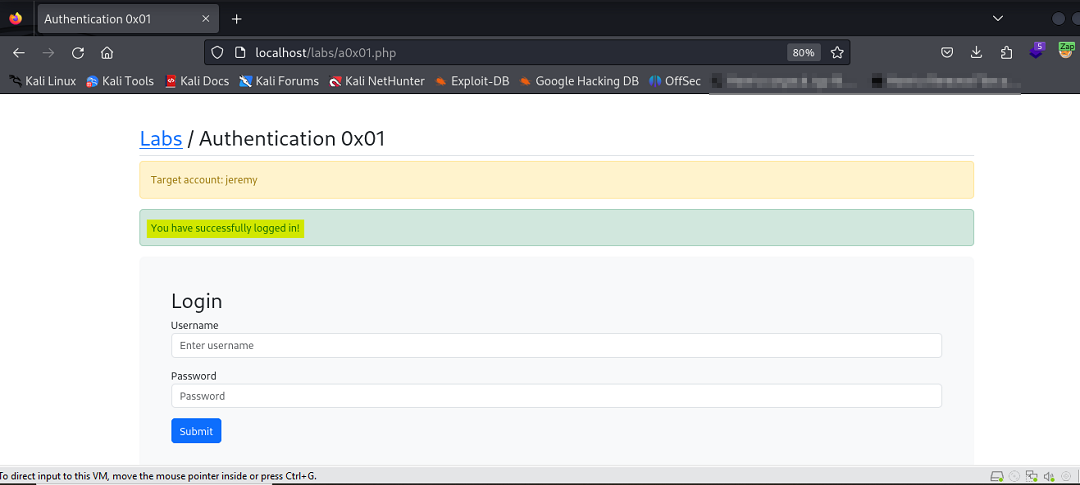
We’re provided with a username and tasked with brute-forcing the application to uncover the password. When faced with a brute-forcing scenario as this, be mindful of a lock-out policy which, in our case there isn’t one.
Entering an incorrect password returns a message revealing that our credentials are invalid.
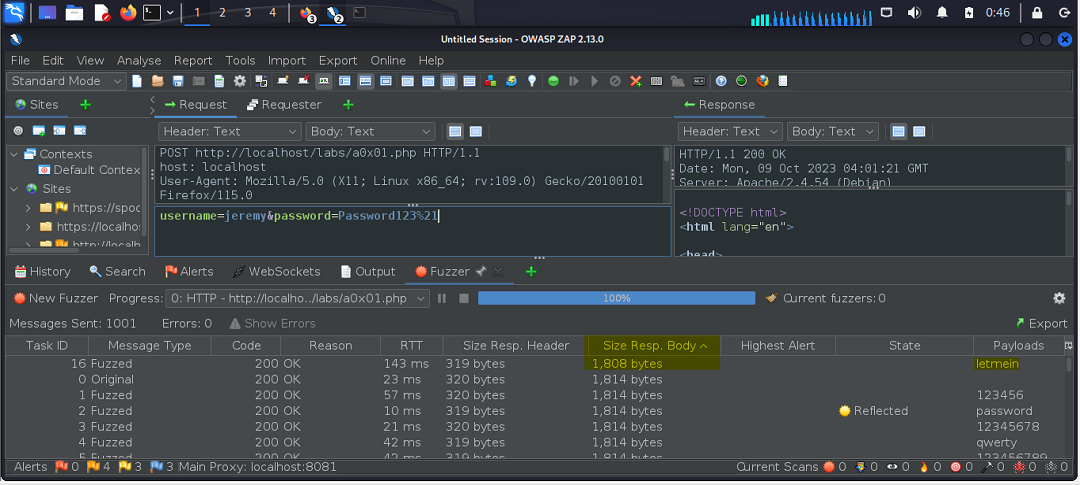
We then utilized our proxy to intercept the request, fuzz the password position/value, and brute-force the credentials using the same word list the instructor used in the course. (The SecLists wordlist ships with Kali but can also be downloaded online.)
As shown in the following screenshots, we found the correct password.
Take special note of the size of the response body. Notice how the incorrect attemps were all roughly the same length but the correct attempt is noticeably different.
Sorting the Size Response Body column, the difference is significantly apparent.
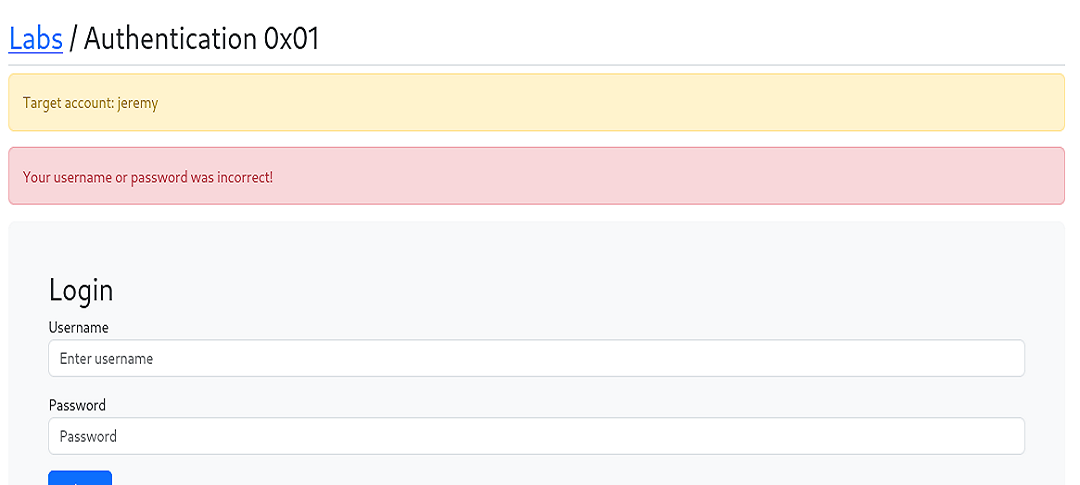
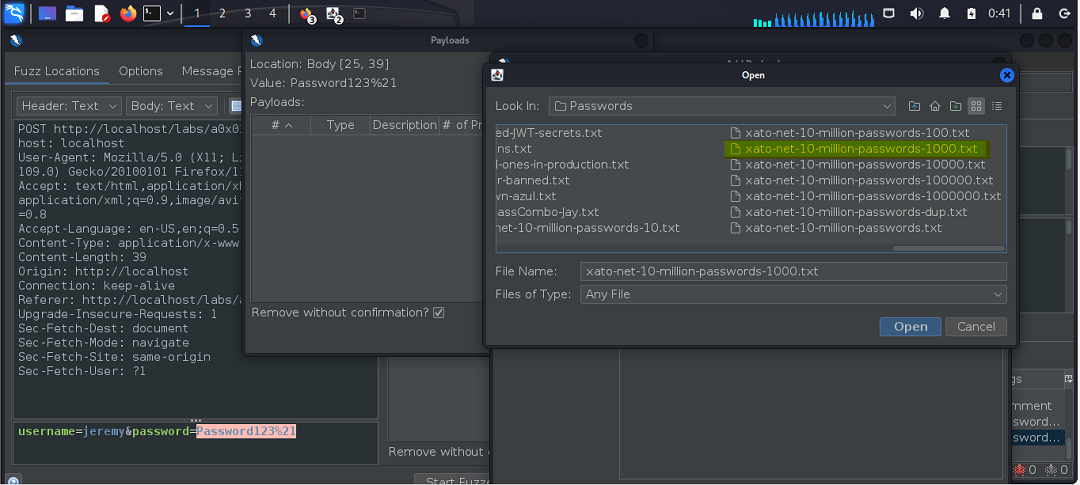
Auth 0x02
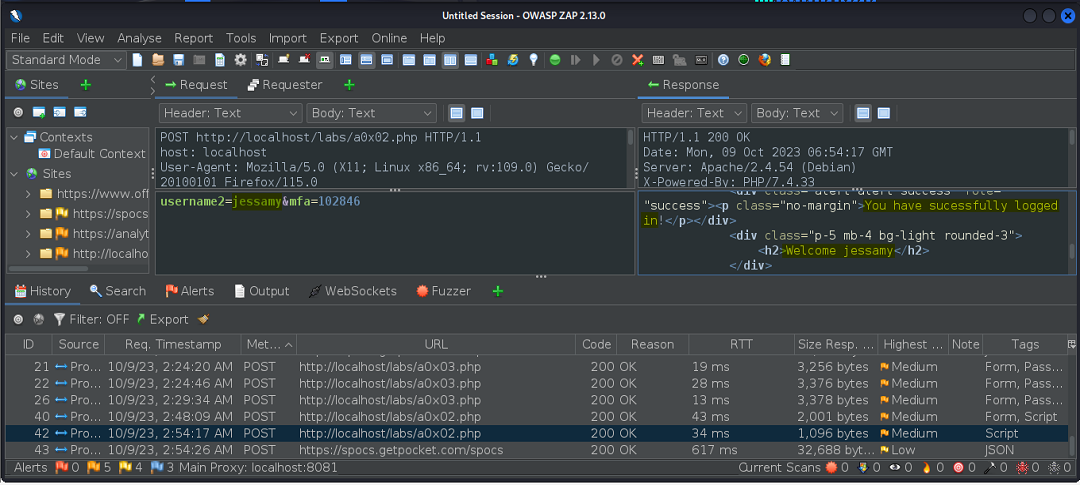
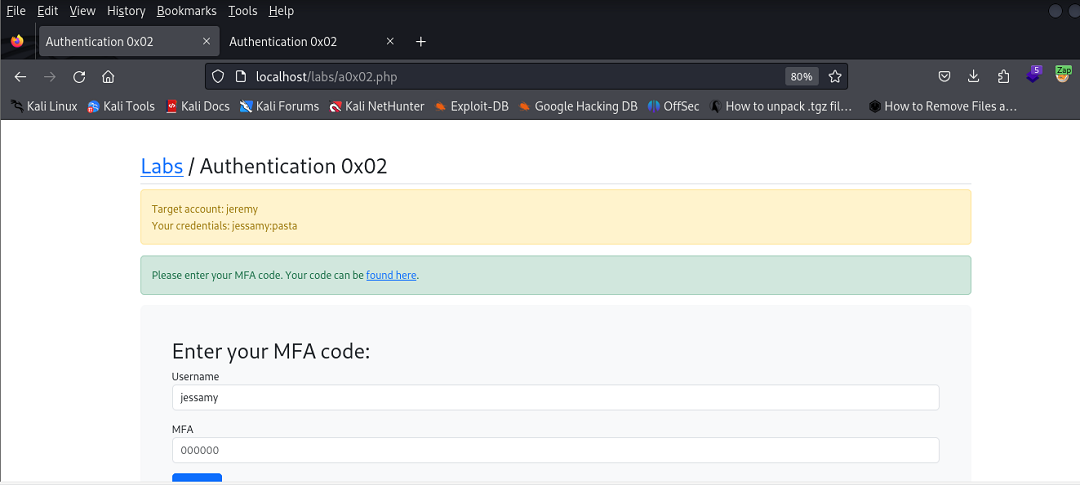
The next exercise covered a case of MFA (Multi-Factor Authentication). Here the user supplies a username and password, then is provided with a link to retrieve a login code.
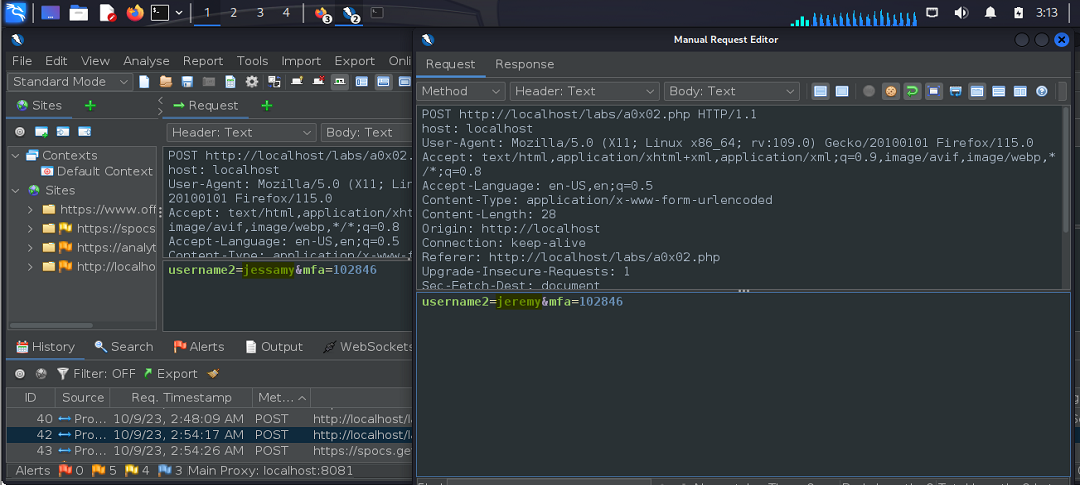
In such an instance as this where the username control gets pre-populated, one way to compromise the app would be to intercept the POST request made after supplying the required second layer of the authentication process, the code.
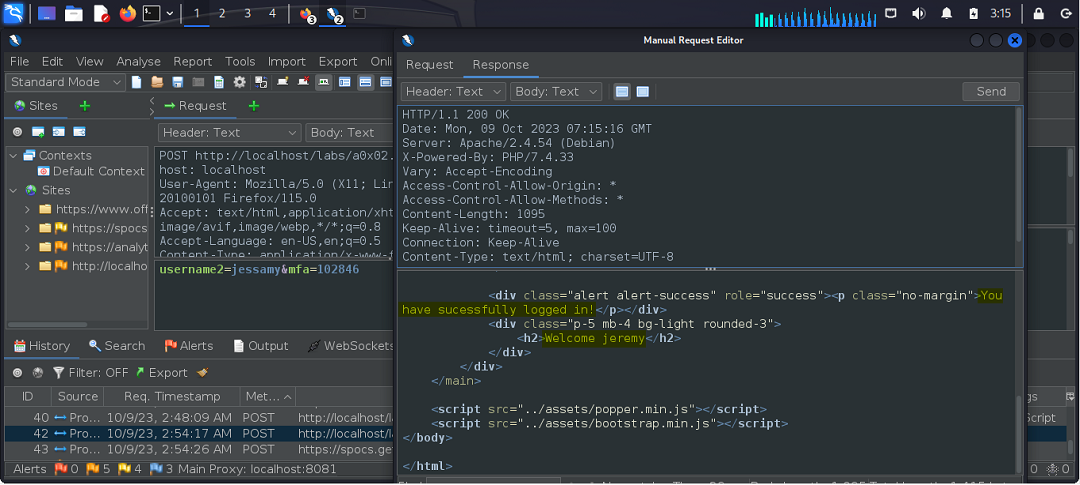
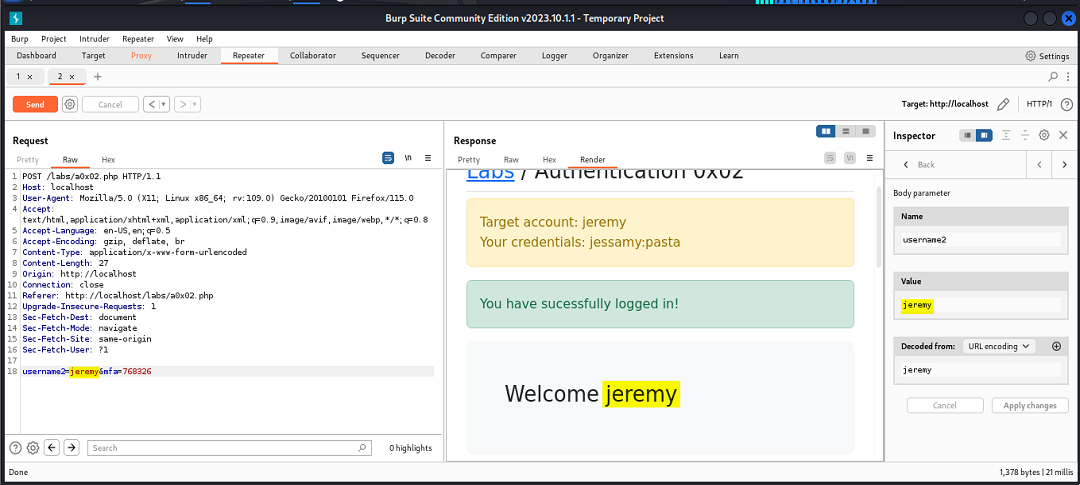
If a valid username/password combination is supplied, a code can then be retrieved; however, intercepting the request and changing the username parameter to a different user, we’re able to subvert the logic and be authenticated into the account of a different user.
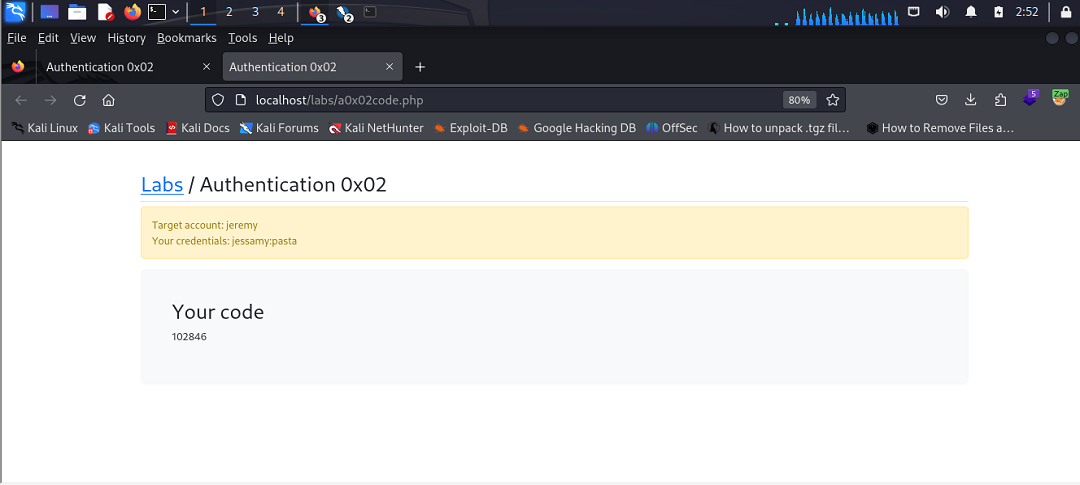
Note: the exercise required the tester to use the name “Jeremy” as the value but this will work regardless what name is used.
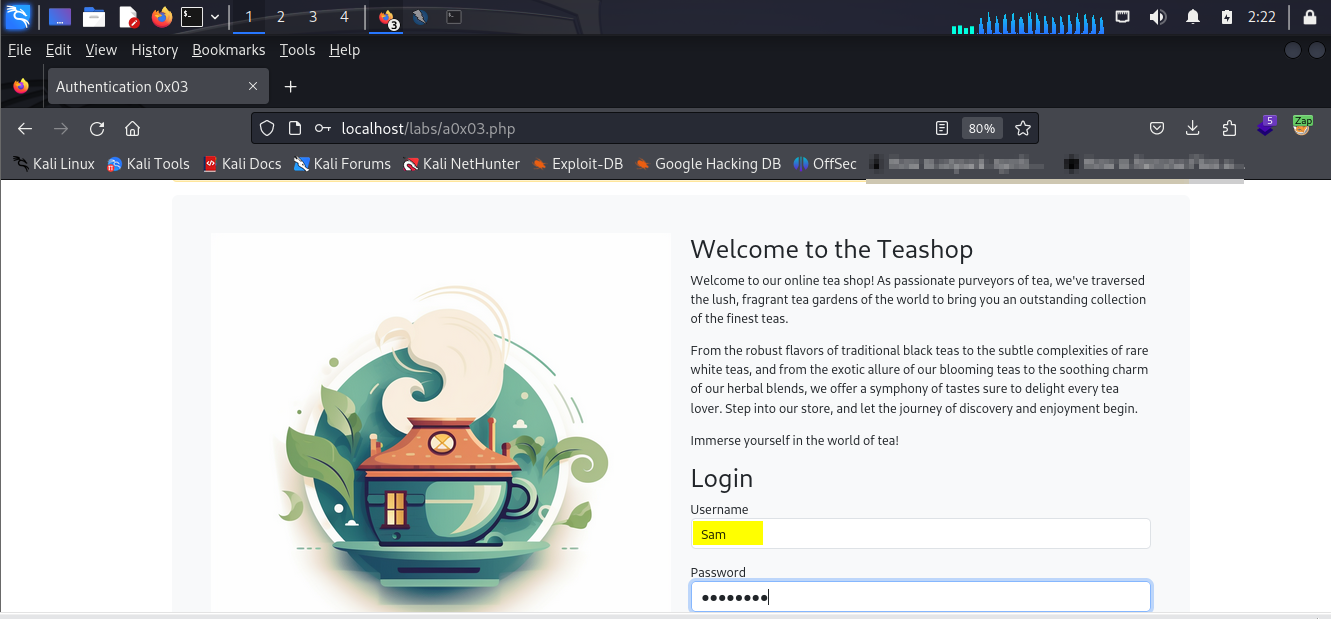
Auth 0x03
The last one we’re covering in this post also turns out to be a challenge. Not a challenge in the sense that it challenges you, but the literal challenge of the first 3 exercises.
A little disclaimer here, just listening to the hint the instructor put out was enough for me to authenticate in on the second attempt.
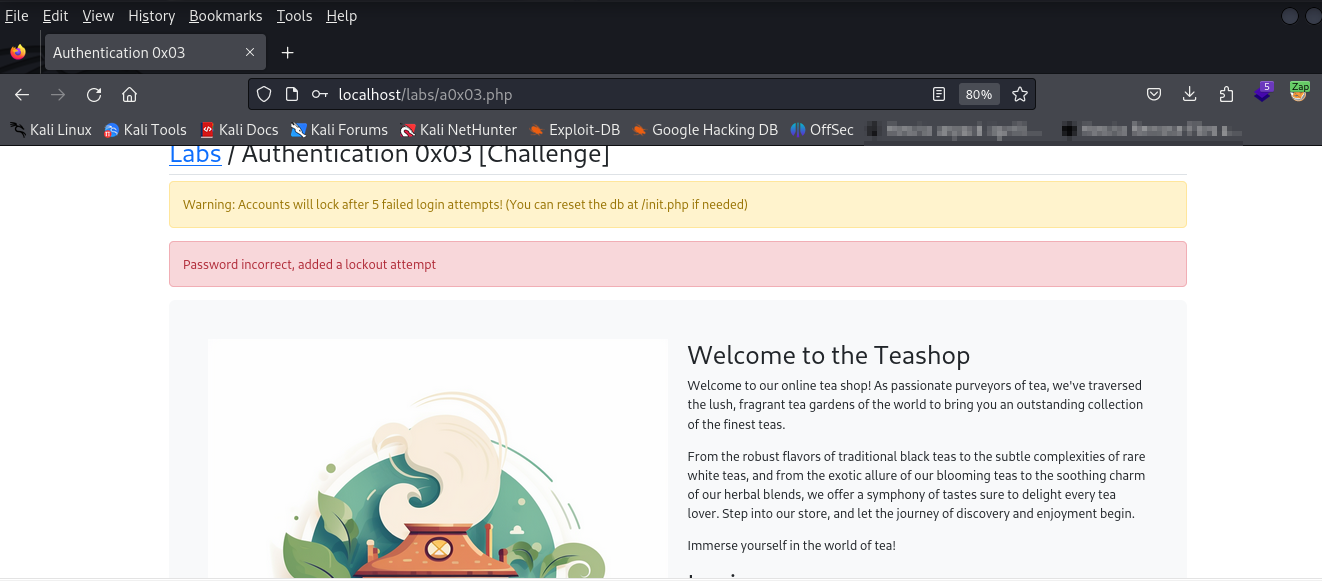
I really liked this challenge because as simple as it may have seemed to solve, it introduces an account lock-out control which forces us to tweak our approach to brute-forcing.
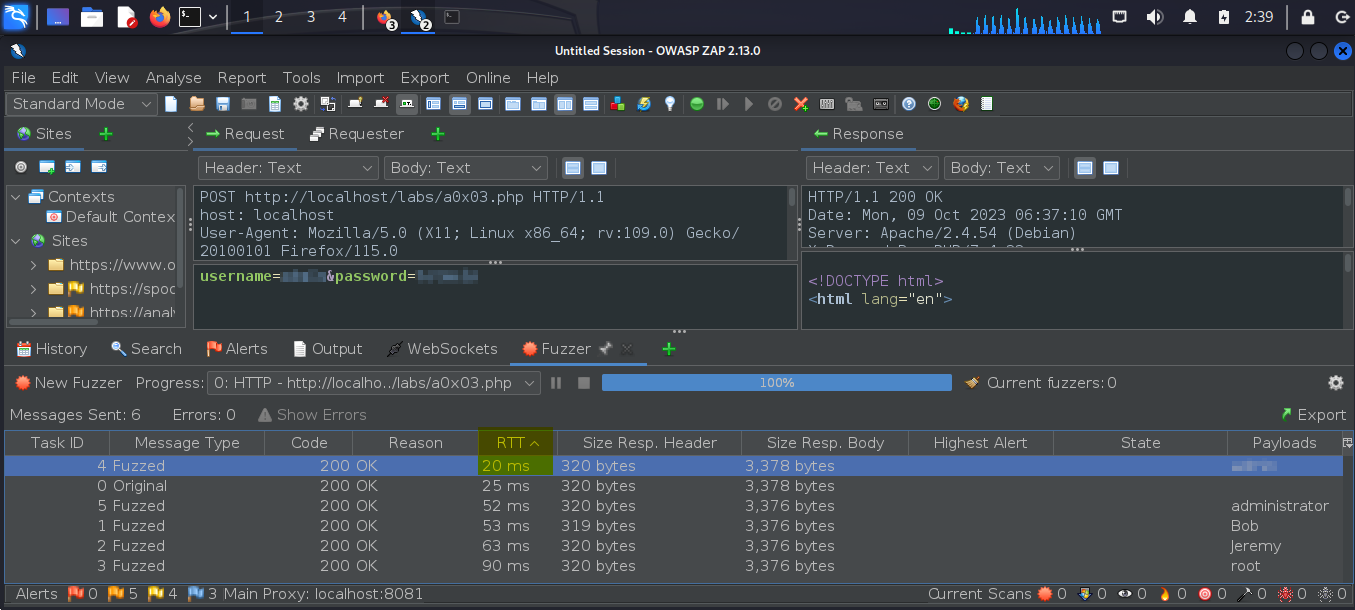
Where normally our attack would center around brute-forcing the password, this challenge calls attention to the username being the center of our attack.
Again, here note the difference between the RTT of the correct and incorrect attemps, which are even more apparent when the column is sorted.
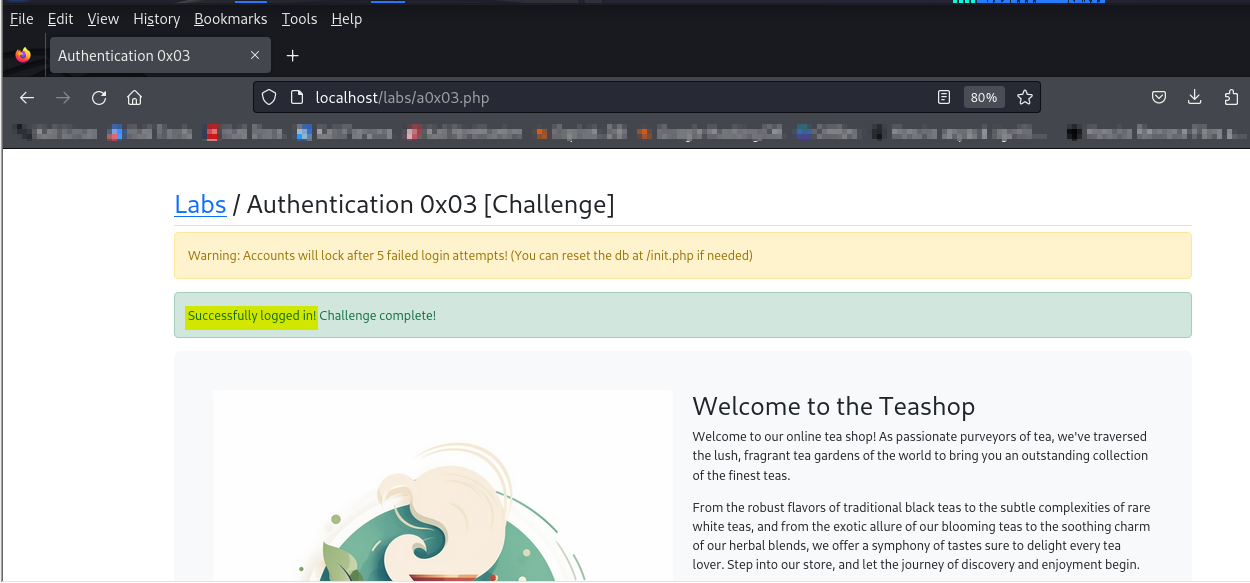
In conclusion, remember that Authentication defines who is allowed while Authorization defines what is allowed.
Big ups to TCM Academy for blessing us with another gem. Shouts out to Heath and special shouts go out to Crypto Cat and Alex Olsen who I hadn’t checked out until this course.
I realize this post was long but there was a lot to catch up on considering the amount of time we’ve been away. Hopefully, I haven’t offended anyone and if I have then that’s on me, I apologize. To anyone who I may have inspired or helped that’s praises be to the universe and to the Hacker God. ![]()
Be sure to return here in a few days for Part 2 of Authentication and Authorization Attacks.
Hack On, ladz & gentz!


