SQL Injection – Fundamentals
26
September, 2022
Days 55 – 57
SQL Injection – Fundamentals
100 Days of Hacking
Photo Cred –> Caspar_Rubin
SQL Injections
In this Days of Hacking session, we covered SQL and SQL Injections.
To learn more about the subject in depth, please have a look at the following – HTB’s Bug Bounty Hunter Job Role Path
Here’s a summary of what was covered:
- Basics of databases and their different types
- Basics of SQL and MySQL
- Basic statements and operators in MySQL and how to use them
- What are SQL injections, and how can we use them
- Use SQL injections to subvert the web application logic and bypass authentication
- Use UNION SQL injections to dump data from different tables and databases within the DMBS
- Use SQL injections to read files of the back-end server
- Use SQL injections to write a web shell on the back-end server and gain remote control over it
- How to mitigate such SQL injections and patch your code
Subverting Query Logic
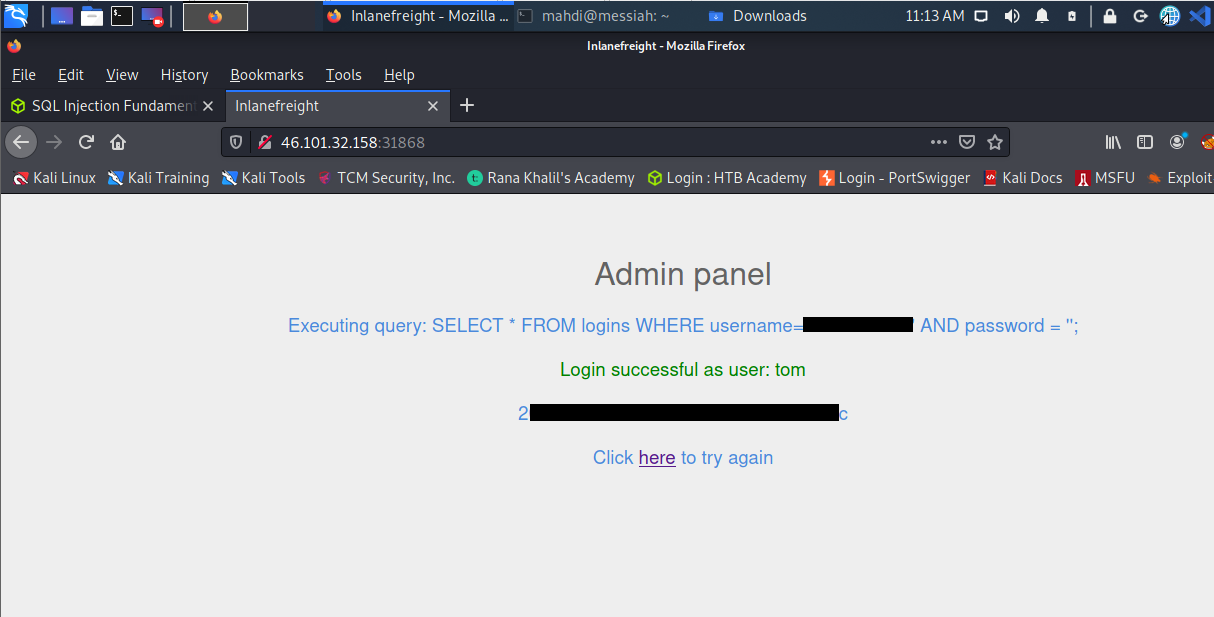
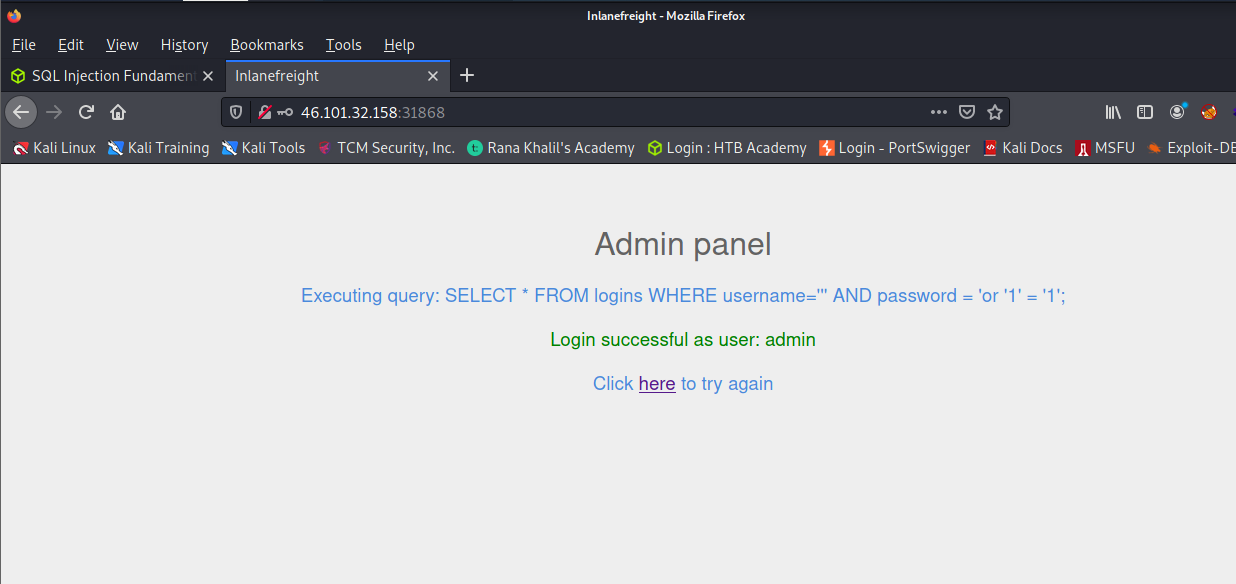
Here we were to try logging in as the user ‘tom’ and obtaining the flag value.
Day 56
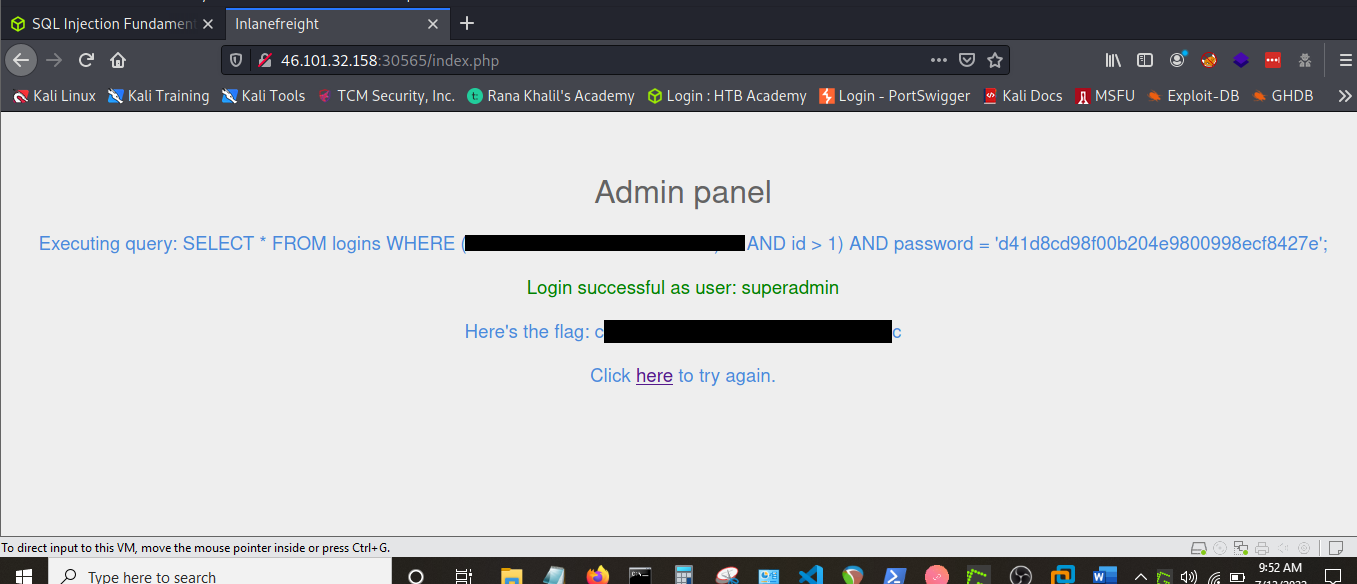
Using comments
Here we were to login as the user with the id 5 to get the flag.
Day 57
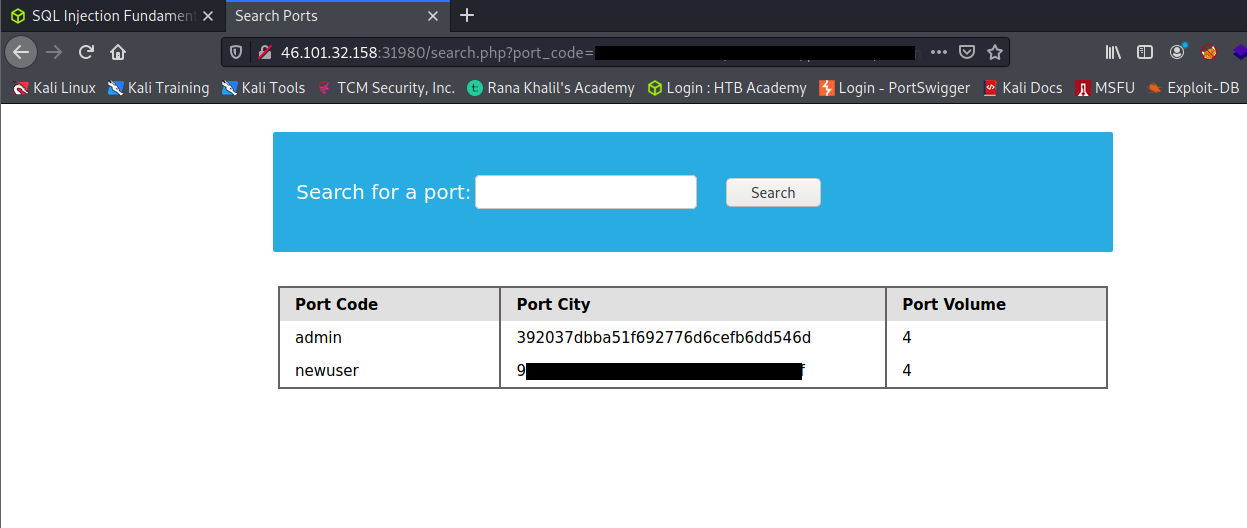
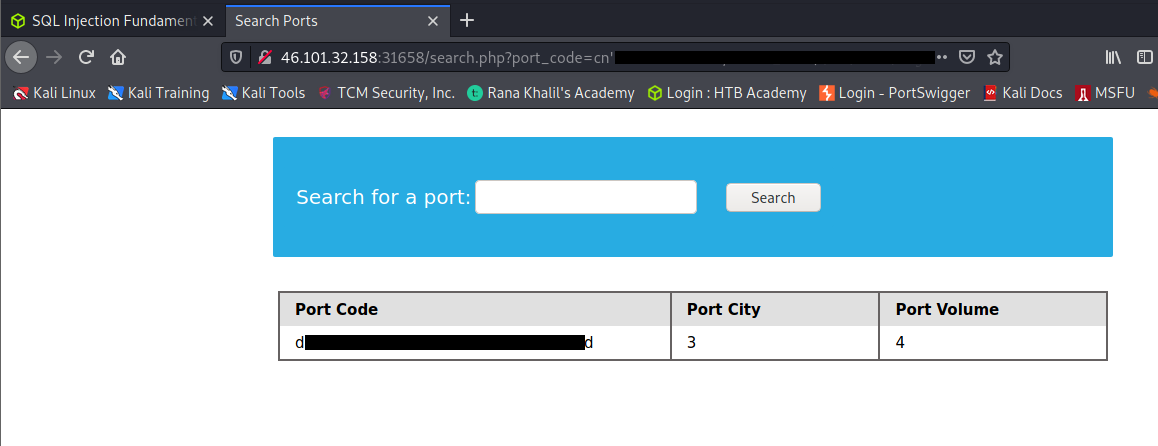
Database Enumeration
Here we were to find the password hash for ‘newuser’ stored in the ‘users’ table in the ‘ilfreight’ database?
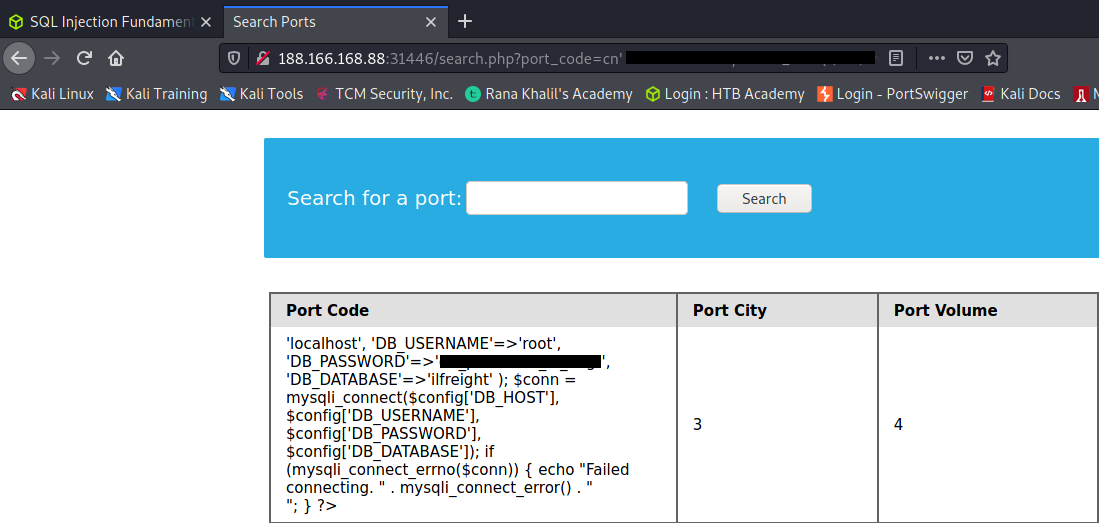
Reading Files
We see in the above PHP code that ‘$conn’ is not defined, so it must be imported using the PHP include command. Check the imported page to obtain the database password.
Writing Files
Here we were to find the flag by using a webshell.
Now that we’ve covered the basics of SQL and know what SQL Injections are, how to find and exploit them, next we’ll look at tool that can help us automate some of the heavy lifting.
As always thanks for reading if you’ve made it this far. You’re sincerely appreciated.
Hack On, Ladz & Gentz!
Many people who have been called hackers, especially by the media, or who have gotten in trouble for “hacking” were not, in fact, hackers. – Lesson 1: Being a Hacker


